Introduction
The lean security team is responsible for infrastructure, end-point, and application security. The main goal of the security team is to provide the engineering organization with the appropriate security data (such as security issues, fix rates, etc.) so that the engineering organization can meet its Service Level Objectives (SLOs).
To achieve this goal on the application security side, Thinkific wanted to provide security guardrails for developers and not block developers’ pull requests (PRs) unless high-confidence or reachable issues were detected in their code. Thus, the application security team can ensure that the development velocity does not slow down because of the security process.
Challenges before Semgrep
The three major challenges that Thinkific faced with the previous application security products were: 1. The scans were very slow (took hours on monorepo), 2. The results were extremely noisy (high false positive rate), and 3. They could not properly configure the products to fit Thinkific’s environment. Due to these issues, even when a developer changes a few lines of code, the application security products would take hours before surfacing issues (if any). Sometimes, even after taking hours to scan, the scan would fail without any additional information to debug the reason for the failure.
In addition to this process being frustrating for the security team, these products became a blocker for fast development. So, the slow scan time and noisy results made these products ineffective in meeting the security team’s goals.
Discovering Semgrep
Aleksandr Krasnov, Staff Security Engineer at Thinkific, first came across Semgrep after talking with Clint Gibler. The ability to easily customize Semgrep rules immediately caught Alek’s attention. Alek could easily tweak a Semgrep rule message (which shows up as a PR comment for developers) so that developers understand the context of a security issue.
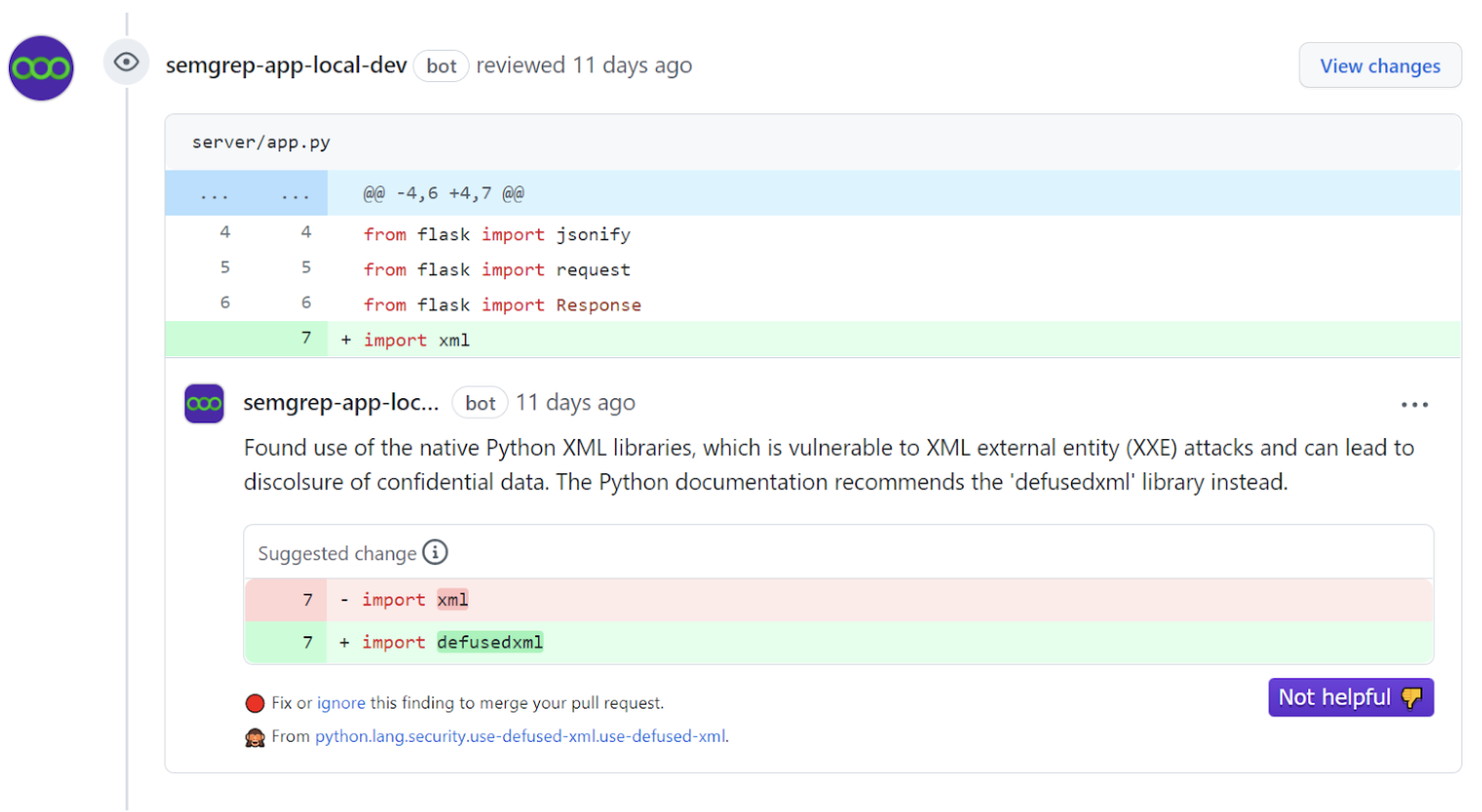 Example of what a developer would see as a pull request (PR) comment for the above rule
Example of what a developer would see as a pull request (PR) comment for the above rule
Effectively communicating security issues to developers
To keep up the fast software development cadence, the ability to control which security issues are surfaced to developers is critical. Thikific uses Semgrep Policies to manage security touchpoints with developers. The following workflow shows how Thinkific (and many Semgrep Code users) use Policies.
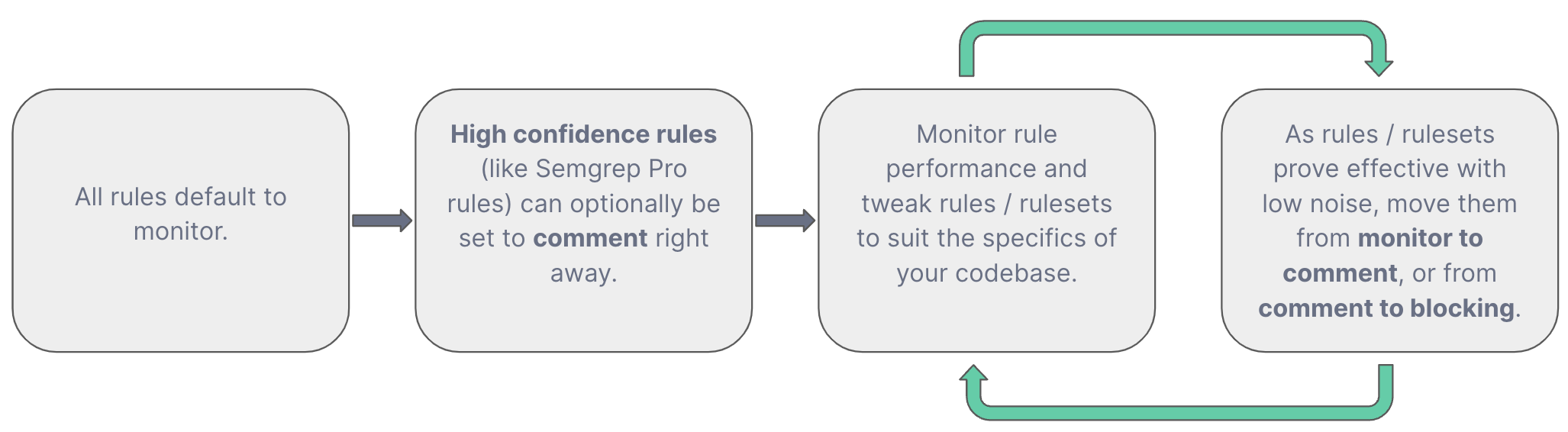
According to Alek, getting the right code scanner in place is not the hardest part of the job. Getting all developers aligned on the SAST product and making sure they use it - is the hardest part of the job. Alek achieved this using Semgrep Code and Thinkific’s security champions. Thinkific invests a lot in its security champions program because it wants efficient processes in place when developers liaison with security. So, with Semgrep Code, Thinkific’s developers see a high percentage of true positives as PR comments from Semgrep, and they also have the appropriate context to fix the security issue.
“Getting the developers aligned on a SAST product and making them use it is the hardest part of the job for an AppSec Engineer. We were able to achieve this with Semgrep Code.”
Aleksandr Krasnov, Staff Security Engineer, Thinkific
Reachability and Semgrep Supply Chain
Semgrep Supply Chain (Semgrep’s SCA product) uses lockfiles (instead of manifest files) to do reachability analysis. Using lockfiles to do reachability caught Alek’s attention because this approach provides more visibility and fewer false positives. Thinkific reduced the noise by 85% using Semgrep Supply Chain (compared to the previous tools they used)! Due to this high reduction in noise, developers fix the open source dependency issues within the appropriate SLA time frame.
While getting an awesome scanner like Semgrep Code for our SAST was great, Reachability Analysis via Semgrep Supply Chain was the cherry on top.
Aleksandr Krasnov, Staff Security Engineer, Thinkific

Looking forward
Thinkific is excited about Semgrep Assistant (using GPT to get a second opinion on Semgrep Code’s findings). The initial results have been promising, but the security team wants to test it more before rolling it out to developers. Thinkific has found Semgrep to be an invaluable part of its security program because using Semgrep has enabled it to fix issues that matter while commuting with developers more efficiently.
About
Semgrep enables teams to use industry-leading AI-assisted static application security testing (SAST), supply chain dependency scanning (SCA), and secrets detection. The Semgrep AppSec Platform is built for teams that struggle with noise by helping development teams apply secure coding practices.




