At Semgrep, we recognize that security of your software supply chain is critical — but it shouldn’t come at the cost of developer productivity. With Semgrep’s Supply Chain Policies, AppSec teams have fine-grained controls and can take a precise approach to security policy management. The result? Strengthened security measures seamlessly integrated into CI/CD workflows, ensuring developers stay productive without unnecessary interruptions or friction.
The need for granular, developer-friendly security
Many security tools on the market enforce rigid, one-size-fits-all policies that overwhelm developers with unnecessary alerts, slow down workflows, and fail to prioritize real risks.These inefficiencies lead to wasted effort, security fatigue, and slower development cycles. We’ve listened to our customers and introduced Semgrep’s Supply Chain Policies to solve real problems by offering fine-grained control over your security settings. Whether it’s blocking the most critical pull requests (PRs), Supply Chain Policies allows you to address critical vulnerabilities while allowing developers to stay productive.
.png)
1. Granular control where it matters
Establish precise configuration of supply chain policies based on:
Repo-level control: Roll out PR blocking team-by-team or set different policies on critical repositories to match your organization’s needs. These controls allow fine-grained scoping of policies to ensure high-priority repositories receive focused security measures.
Reachability: Apply stricter controls for reachable vulnerabilities that actually pose a direct risk to your code.This approach prevents unnecessary disruptions, allowing developers to stay productive while addressing the most critical risks.
Severity: Block or comment on pull requests or merge requests for critical and high vulnerabilities without notification overload and guide developers on necessary fixes.
Upgrade availability: Show developers only the vulnerabilities with available upgrade paths, building trust with your development team
Transitivity: Vulnerabilities in direct dependencies pose a bigger risk, and Semgrep helps prioritize them over transitive ones for faster, more effective fixes.
Exploit Prediction Scoring System (EPSS): Semgrep’s policies optionally use EPSS to prioritize vulnerabilities based on real-world exploitability, reducing noise and focusing on the most likely threats.
2. Time savings for application security teams
Semgrep’s automation streamlines workflows by enabling pull request (PR) blocking or commenting, which reduces manual ticket creation.
3. Streamlined developer workflows
Irrelevant alerts slow developers down. Through more granularity in developer-facing notifications and blocking settings, Supply Chain Policy Automation reduces noise, so developers see what matters most.
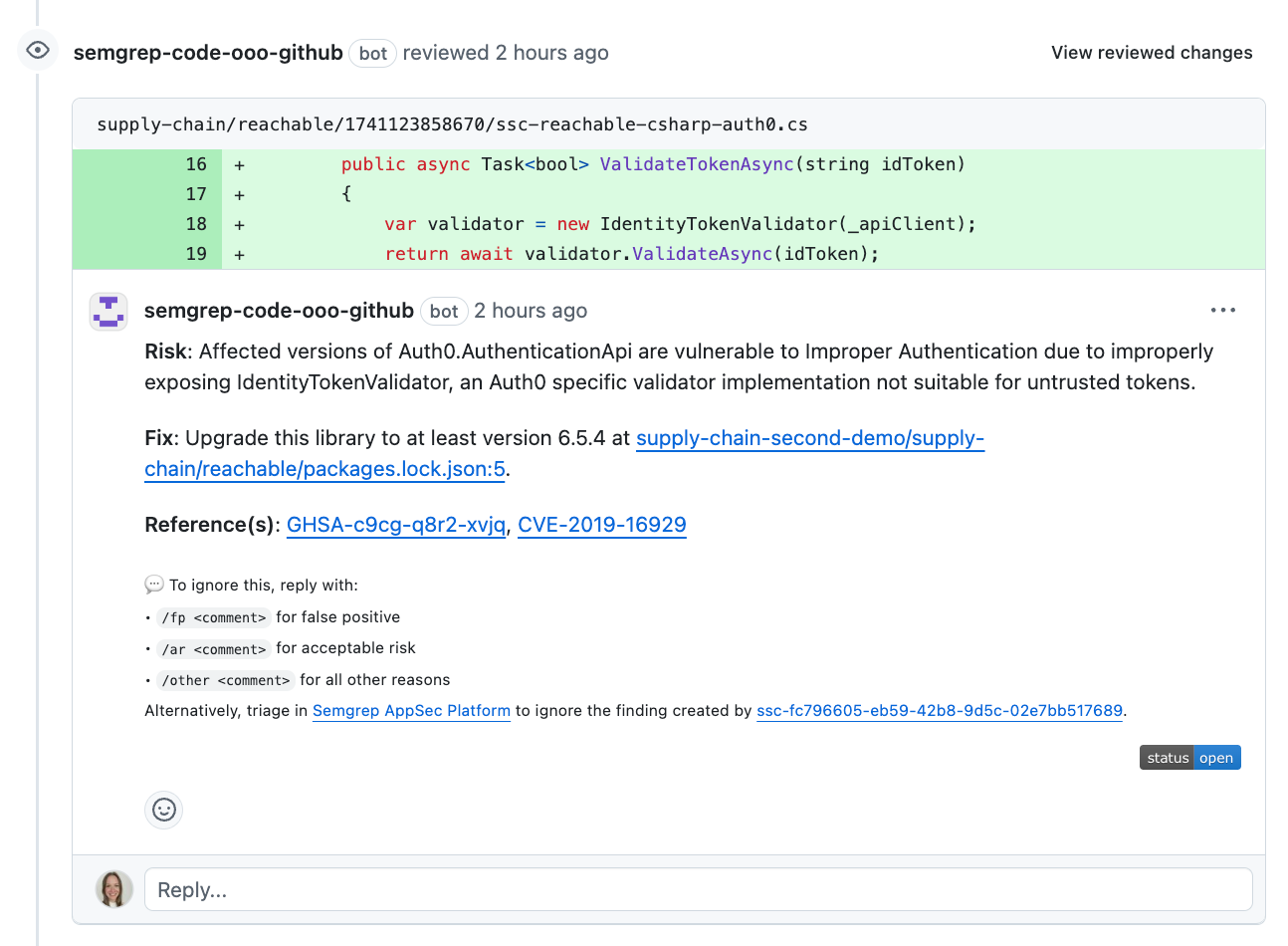 The result of blocking a pull request in Github with Supply Chain policies
The result of blocking a pull request in Github with Supply Chain policies
4. Enterprise-ready flexibility & seamless adoption
Organizations at scale leverage this feature to match their security controls to their business needs. Whether it’s customizing PR comments or fine-tuning blocking thresholds, this feature adapts to your team’s unique workflows. Developers and AppSec teams can roll out policies gradually starting with security-friendly engineering teams before expanding to the broader organization, ensuring flexibility without disruption.
Real-world use cases
For AppSec teams, Supply Chain Policies becomes a clean solution for bucketing code across your environment by risk level, applying stricter or less strict controls where needed. First and foremost, set stricter controls for sensitive and untrusted code. Critical production services with data access are naturally more sensitive, as is anything running in production. Any open source projects, code we inherited yesterday through an acquisition, or code we haven’t yet been able to assess is relatively untrusted. These projects may require stricter security checks such as blocking pull or merge requests. On the other hand, lower risk code can be secured in a lighter weight manner. Any internal tools, development and test repositories, and code owned by teams that manage security themselves are relatively more trusted. For these kinds of repos, commenting on PRs is easier and less disruptive for developers, allowing them to focus on writing code without slowing down.
Developers get real-time alerts about serious security issues in their code review process, so they can fix the significant risks first, making security more efficient and less time-consuming. Semgrep enables teams to set different security rules depending on whether a repository is open-source or private/internal. Open-source projects may require stricter security checks to prevent public vulnerabilities, while private repositories can have policies that align with internal workflows. This ensures security is easier and less disruptive for developers, allowing them to focus on writing code without slowing them down.
Looking ahead
Semgrep’s Supply Chain Policies are already making an impact. Future updates will provide even greater flexibility, enabling AppSec teams to tune their security policies as needed to stay secure without slowing down development.
Start securing smarter
Ready to take your supply chain security to the next level? Schedule a demo to see how Semgrep’s Supply Chain Policies can transform your security workflows. At Semgrep, we believe security should empower, not hinder.





