Detect
Semgrep Secrets can scan thousands of lines of code and look for hardcoded secrets, API keys, and other sensitive data in a few minutes using Semantic Analysis, entropy analysis, and regex.
Go beyond regex: leverage Semantic Analysis, entropy analysis, and validation to accurately detect and fix secrets.
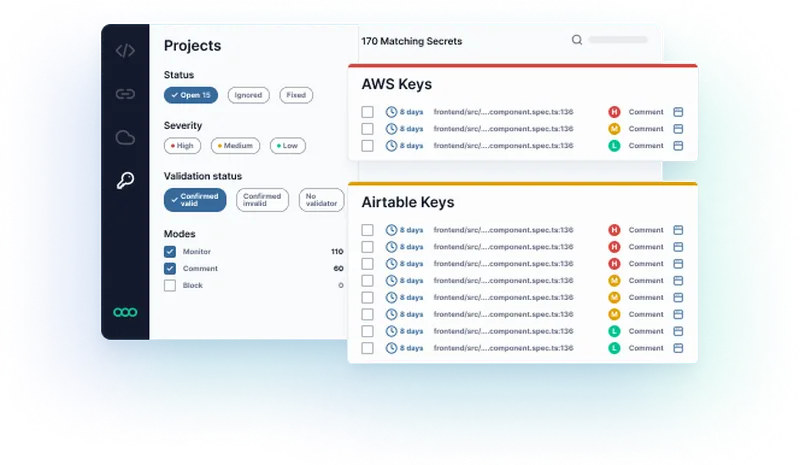


Leverage Semgrep’s data flow engine to understand what credentials exist and how they are being used (Semantic Analysis)
Prioritize valid credentials and reduce false positives using Semgrep’s post-processor
Detect secrets that are specific to your internal services by writing custom rules
Warn developers about secrets in their editor or code review workflows
Use pre-commit hooks to prevent secrets from being committed to Git repositories
Leverage semantic analysis to reduce alert fatigue and minimize false positives
Semgrep Secrets uses OSS + Pro Engines to find secrets specific to your code.
Semgrep Secrets can scan thousands of lines of code and look for hardcoded secrets, API keys, and other sensitive data in a few minutes using Semantic Analysis, entropy analysis, and regex.
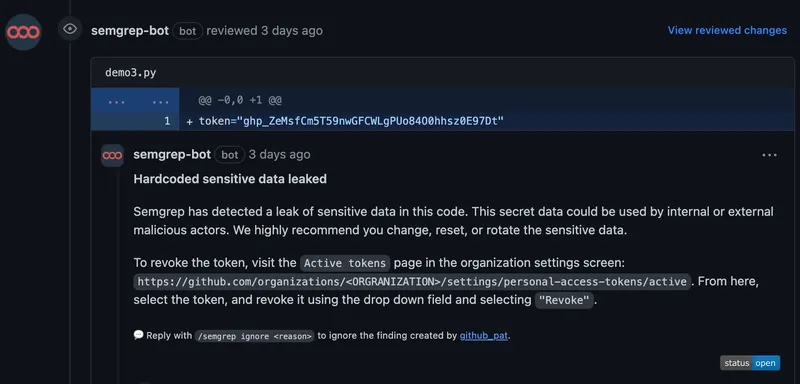
Semgrep sends a request to the corresponding service (e.g., AWS, Slack, or GitHub) to determine if the token is still valid. This happens locally within your infrastructure; we don’t send the secret to Semgrep’s servers.
Validated secrets are surfaced to developers in their workflow as PR comments so that developers can fix them as soon as possible.
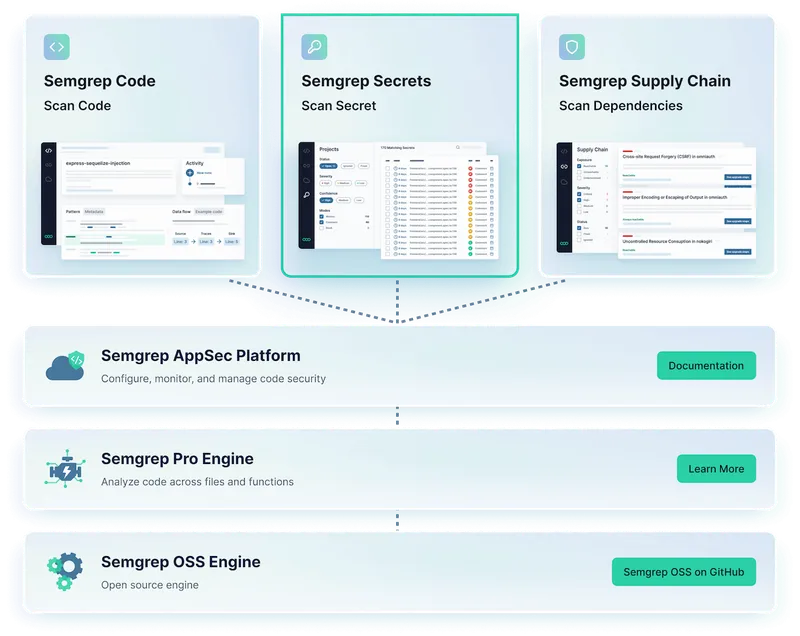
Find and remediate security issues in your code, software supply chain, and secrets using one platform
Get consistently high-quality findings across all products since they leverage the same underlying (Pro + OSS) Engines
Figmates get actionable security feedback in their PRs, while rule analytics give the security team feedback on the effectiveness of our rules. The simple syntax lets us extend Semgrep to catch new patterns, going from idea to live in an hour.
