Announcing Semgrep's Series D
We want using Semgrep to be like hiring an AppSec engineer to do the boring work. To be the best platform for code scanning, Semgrep must go beyond finding issues. It must autonomously remove noise, commit fixes, and communicate with developers – freeing up security teams to work on high-impact human work like crafting secure guardrails and discovering novel vulnerabilities. Our vision is autonomous (but still transparent and deterministic) security decision-making at scale.
I'm delighted to announce we’ve raised a Series D to help us reach this goal, led by Menlo Ventures with participation from existing investors Felicis Ventures, Harpoon Ventures, Lightspeed Venture Partners, Redpoint Ventures, and Sequoia Capital.
Why the mission matters
Software is eating the world—and AI is accelerating that (check out "vibe coding"). We often talk with security teams who are stretched thin—outnumbered by developers 100:1. If code volume grows as fast as code generation companies predict, that ratio will get far worse. Imagine sleepless security teams trying to review every line of LLM-generated code, rapidly switching mental contexts between different projects and frameworks.
Just improving detection quality to eliminate false positives isn't enough: we need to programmatically eliminate entire classes of issues (OWASP Top Ten is a great start) to have a chance at catching up. If a self-driving car crashes, the entire fleet learns from it; however security bugs are often fixed in isolation across (and even within) companies. To make progress we need to see security as a platform engineering exercise, rather than risk mitigation. As Netflix's team says, security should be about "guardrails, not gates." Last year we shipped new features to help get those guardrails in place.
Semgrep's Approach: Extensibility
When we started Semgrep, a few big tech companies knew that extensibility—building on top of a code scanning product as a true platform for guardrails, rather than a vendor's black box—gave the best developer experience and security ROI. We're delighted to be a part of propagating that belief to so many others: in addition to the thousands of rules we've released or maintained for free, we've written tens of thousands of rules internally that join hundreds of thousands of distinct rules written by users and customers.
For individual security engineers and small AppSec teams, we want the open-core Semgrep Community Edition to be the obvious choice for free and fast scanning. It now supports ~40 languages and we find it everywhere from the production pipelines of the world's biggest tech companies to early stage startups.
For larger AppSec teams, Semgrep AppSec Platform should be the lowest-noise, highest signal, and simplest to use option on the market. Since our last funding round, we've shipped powerful features like framework native cross-function and cross-file analysis, reachability analysis for dependency vulnerabilities, and semantic secrets detection.
A fundamental change in AppSec
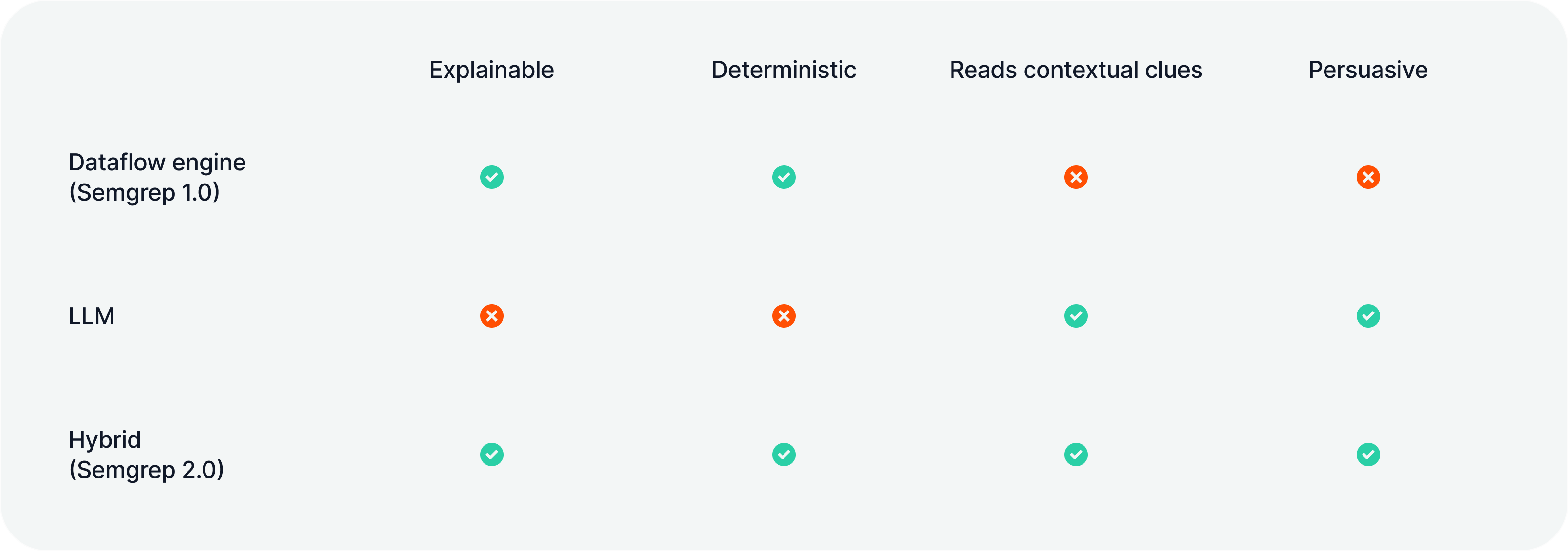
LLMs + extensible dataflow engines (Semgrep 1.0) = Semgrep 2.0
Last year, we combined traditional techniques with LLM capabilities to make something new: a contextualized and deterministic engine.
We’re AI optimists, but LLMs have a number of poor properties for security applications: they're non-deterministic, opaque, prone to hallucination, and perform better on smaller contexts. Yet even when they're wrong, you have to admit they're persuasive and clear at explaining security issues.
Meanwhile, traditional static analysis has its own limitations: it can identify issues so complex humans struggle to understand them, but on its own it ignores contextual clues like comments in code saying "// here's why this is not actually an issue…" or "test" in a file path.
Semgrep Platform is now using a new hybrid engine we call Semgrep 2.0, that maintains both the rule-based determinism of Semgrep 1.0 and the persuasive, context-aware communication of an LLM. Here's how we think about it: