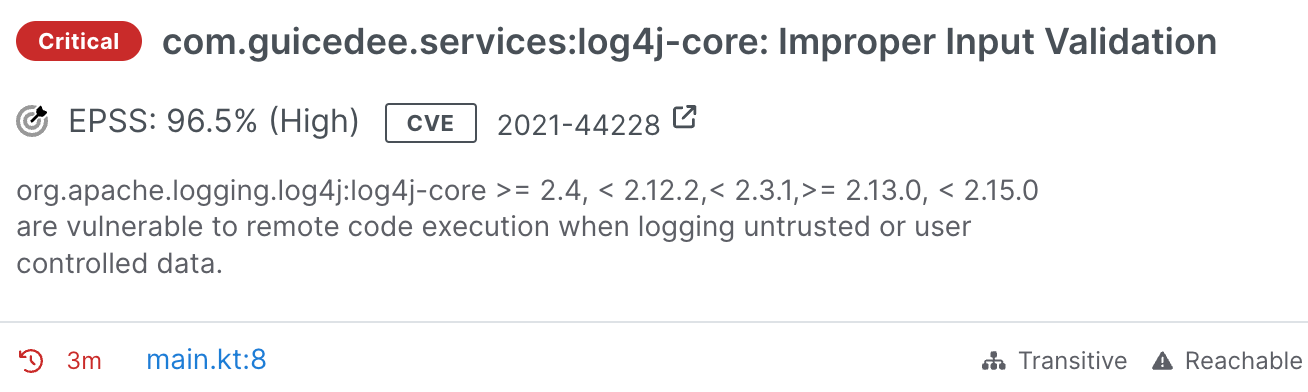
Our goal for reachability analysis with Semgrep Supply Chain is to handle the heavy lifting by pinpointing which vulnerabilities should be prioritized. When a finding is highlighted as reachable, a team of Semgrep Security Researchers has already assessed the security advisory, identified the affected functions, determined when they're vulnerable, and created Semgrep rules to detect if and how those functions are called in your code.
The way that we approach reachability is what makes Semgrep unique; through dataflow reachability we identify not just where, but also how, you are using known affected functions from software dependencies. Through this process, Semgrep reduces noise attributed to false positives by as much as 98%, saving hours of developer time. Adding Kotlin reachability to our arsenal keeps Semgrep in a lead position across the SCA space, with reachability support across 8 different languages.
Why Kotlin Matters
Kotlin has had rapid growth in part due to prevalence in Android development and also because of modern language features, like null safety and concise syntax. It is easy to build clean, maintainable code, and since Kotlin compiles to the same bytecode representation as Java, it’s also easy to integrate into existing Java-based projects. This makes it a powerful choice for Java Virtual Machine (JVM) based applications.
That’s where Semgrep comes in. While Kotlin projects have many of the same dependencies as Java projects, it is still a unique language, and a younger one at that. Security of code in this more nascent language could otherwise be a concern, but our new Kotlin reachability analysis makes your triage of vulnerabilities introduced by Kotlin dependencies easy. We go beyond just identifying the presence of a vulnerable package — but trace vulnerabilities across code paths with precision, to check if your code actually calls vulnerable methods within that package.
How Kotlin Reachability came to Semgrep Supply Chain
The addition of Kotlin reachability reflects our close partnership with customers who have expressed the need for broader coverage. Powered by the Semgrep engine, which supports over 30 languages, Semgrep Supply Chain extends many of our existing reachability rules for Java, to Kotlin while also providing Kotlin specific coverage. A unique differentiator and key advantage of controlling the engine is the ability to fine-tune for cross-language analysis; we are able to link Java and Kotlin code to scan for vulnerabilities in projects using both languages.
Our historical CVE coverage is the same for Kotlin as it is for Java; we cover 80% of all critical severity CVEs since 2017 and 100% of both critical and high severity CVEs since May of 2022.
Looking Ahead
If you’re already scanning Kotlin code, you’re now using Kotlin reachability! If not, make sure you’ve onboarded your Kotlin projects and that they are using a supported lockfile. Currently, we support Gradle (gradle.lockfile) and Maven.
Kotlin reachability marks an important step forward, but we’re not stopping. With support for eight languages and counting, we’re committed to making Semgrep the best solution for reachability analysis in the SCA space. With more languages on the horizon, be sure to stay tuned for more updates as we continue expanding our reachability capabilities.
In the meantime, give Kotlin reachability a try and let us know what you think—we’re always here to help you write more secure code, no matter what language you use.




