Finding vulnerabilities is not the problem anymore. Every code scan, pipeline, and dashboard produces more results than security teams can manage. The real challenge is knowing which vulnerabilities are exploitable, and which are just static noise.
That’s what the new Semgrep & StackHawk integration solves. It connects Semgrep’s static analysis (SAST) with StackHawk’s dynamic testing (DAST) to bring clarity and context to AppSec workflows, helping teams cut through noise, validate what’s exploitable, and focus on fixing what’s real.
Disconnected Testing Creates Confusion
SAST and DAST each play vital roles in securing modern applications. Static analysis finds vulnerabilities early in the development process; dynamic testing shows what can be exploited in a running environment. But when these tools operate independently, they generate duplicate findings and fragmented visibility.
Each tool uses its own identifiers, formats, and scoring models. That means a SQL injection might appear twice — once as a code-level issue, and again as a runtime vulnerability. AppSec engineers then spend hours reconciling reports, cross-referencing IDs, and guessing whether two alerts point to the same flaw. This disconnect wastes time, slows remediation, and erodes trust between development and security teams.
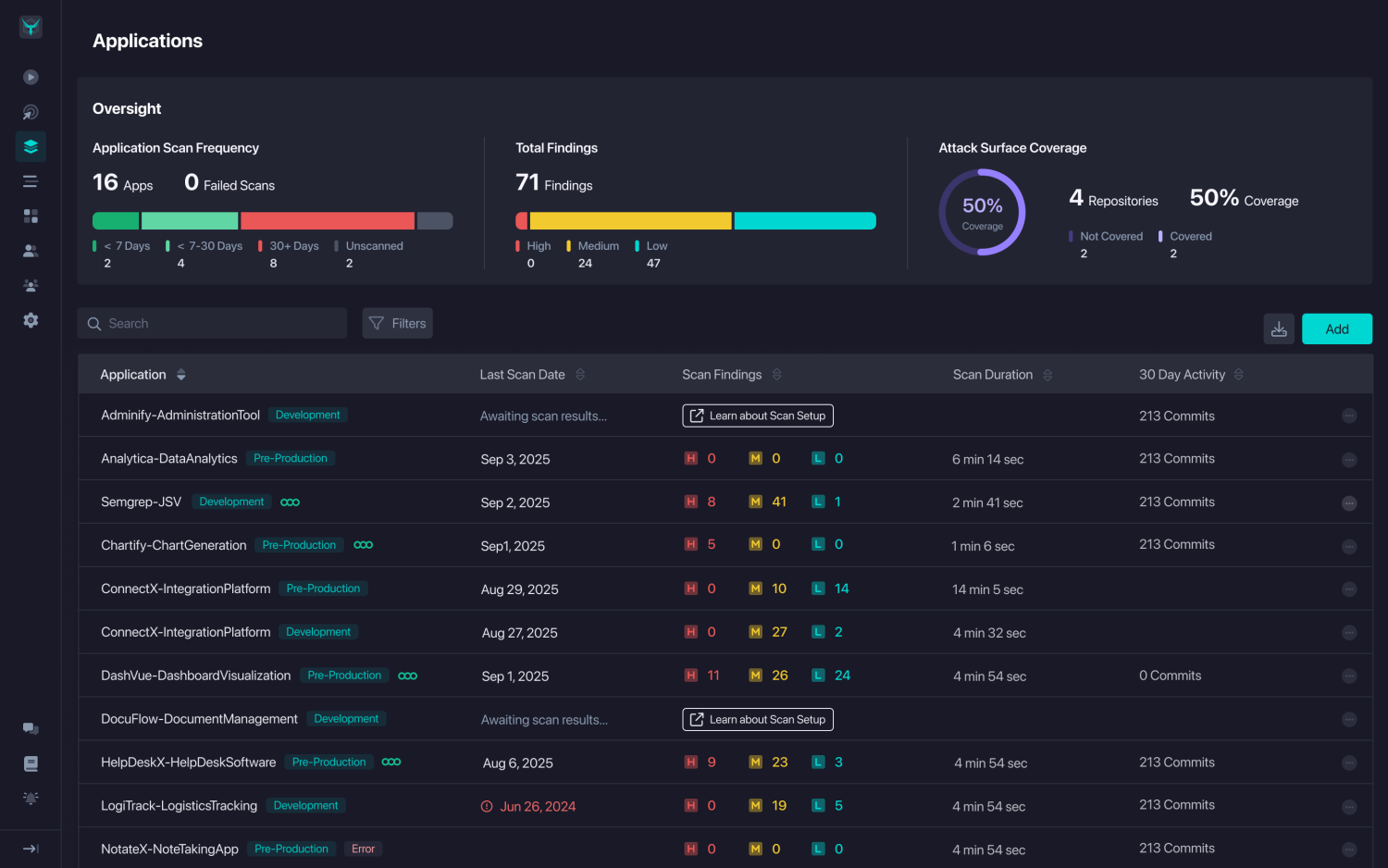 Figure 1: Without correlation, AppSec teams face multiple disconnected scan results across applications and environments.
Figure 1: Without correlation, AppSec teams face multiple disconnected scan results across applications and environments.
Correlation That Drives Action
Semgrep and StackHawk now work together to bring code-level and runtime context into a single, unified view. Semgrep identifies issues directly in code through fast, customizable rules. StackHawk validates what is actually exploitable in APIs and running applications.
By linking these insights automatically, the integration gives AppSec teams the context they have been missing. Instead of two separate alerts, teams see one correlated finding with full traceability from the vulnerable line of code to its runtime impact.
This correlation makes prioritization straightforward:
Correlate findings across SAST and DAST to eliminate duplicate alerts
Prioritize vulnerabilities confirmed as exploitable in production
Accelerate remediation with precise, contextual visibility
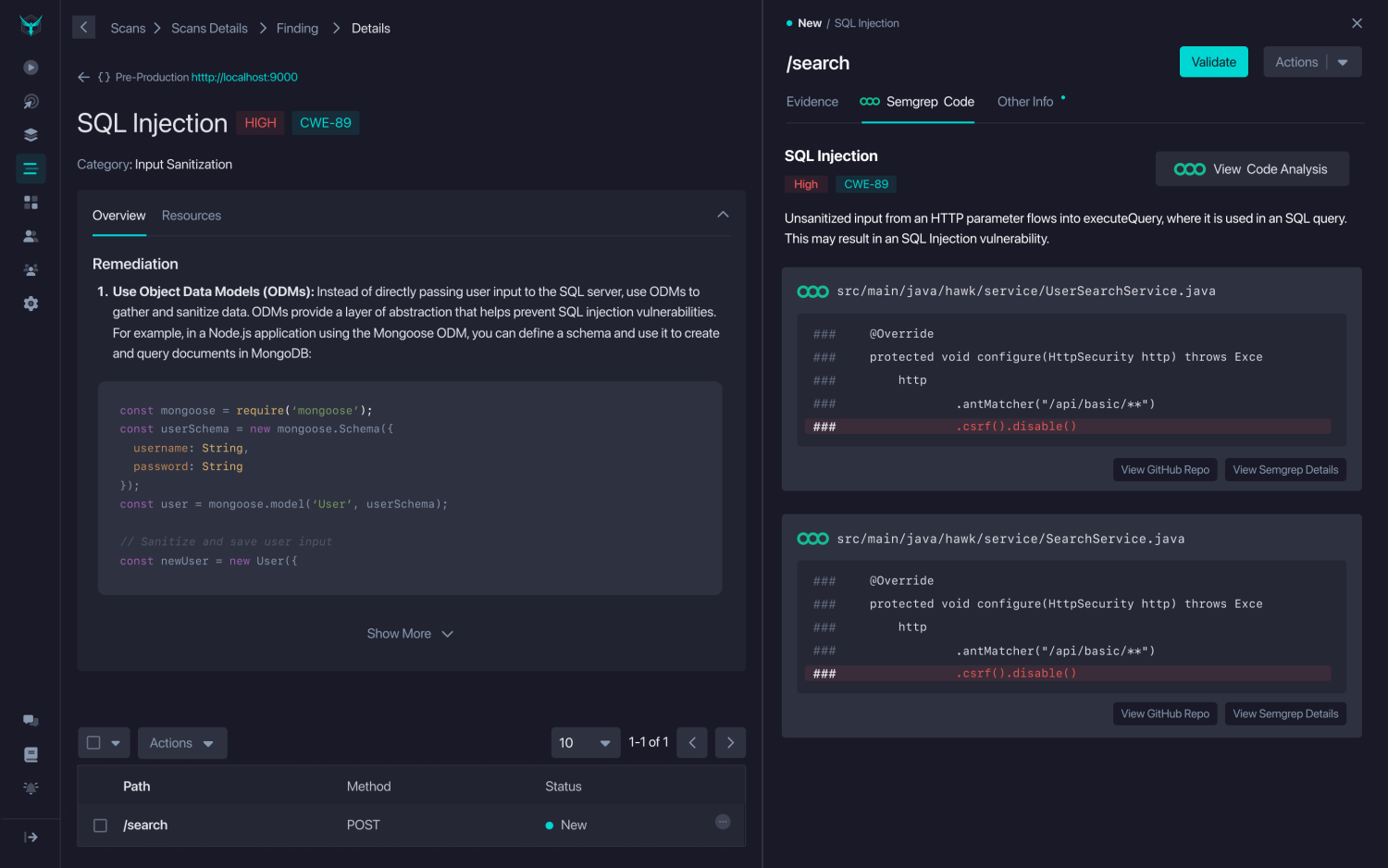 Figure 2: Connecting the Dots; correlated Semgrep findings linked with StackHawk runtime validation provide traceability from code to execution.
Figure 2: Connecting the Dots; correlated Semgrep findings linked with StackHawk runtime validation provide traceability from code to execution.
Bringing Code and Runtime Together
Semgrep scans the codebase during development and CI/CD, identifying potential vulnerabilities.
StackHawk tests the running application or API to determine what is discoverable and exploitable in real environments.
Correlated results connect Semgrep’s static findings with StackHawk’s runtime validation, giving teams a unified view of vulnerability risk.
The outcome is a complete vulnerability record; clear, actionable, and ready for immediate triage. Teams no longer need to cross-reference tools or manually verify duplicates. Everything is aligned from the first scan to the final fix.
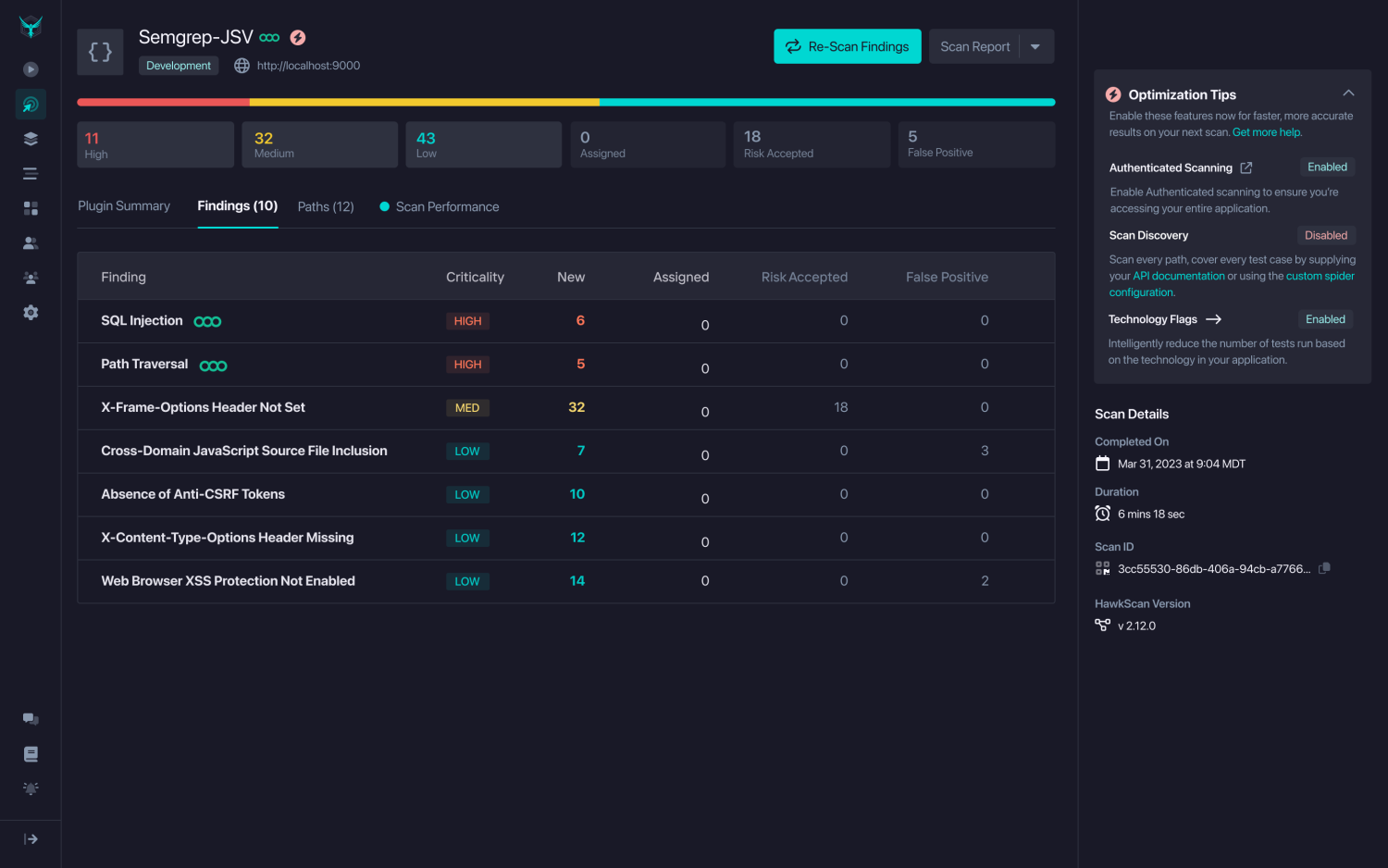 Figure 3: Unified View of Correlated Findings Across Code and Runtime for confident remediation.
Figure 3: Unified View of Correlated Findings Across Code and Runtime for confident remediation.
Why This Integration Matters Today
Software is being written and shipped faster than ever, with AI and automation accelerating development cycles. That speed expands the attack surface and magnifies the cost of noisy, disconnected tools.
By correlating SAST and DAST results automatically, Semgrep helps teams stay focused on exploitable risk, not just potential findings. It turns detection into understanding and replaces manual correlation with precision and confidence. This integration marks an important step forward in AppSec maturity, creating a unified feedback loop where developers and security teams share one source of truth about vulnerability risk.
Get Started
Request a demo to see how Semgrep and StackHawk’s correlated SAST and DAST findings accelerate your remediation decisions.



