The last few months saw a sharp rise in the frequency and severity of supply chain security incidents, where various malicious package versions made their way from trusted package managers downstream to countless organizations and their projects. During such critical severity events, security teams go into all-hands-on-deck mode, fighting fires trying to remove the malicious packages as quickly as possible, as the CISO demands answers and assurances. In about as long as it takes to say Sha1-Hulud, the nature of their work upends from risk mitigation and security hygiene to incident response.
Attack Surface has Also Shifted Left
SCA tools are used to identify all the open source and third party packages your software is using. They were designed to be preventative in nature, allowing AppSec practitioners to manage dependencies, ensure safe upgrades, and generally maintain a low-risk environment.
So when a malicious package is introduced through npm, for example, it seems logical that SCA would help you determine if your environment has imported that affected package.
But as countless organizations have had to painfully learn over the last few months, it turns out that answering this question is not trivial. Identifying all potentially impacted areas in your environment during a critical severity incident has meant generating a SBOM to identify which package versions you’re using, and then auditing those versions to determine whether your projects are affected, before even beginning the remediation process. Compound this with the added complexity that multiple packages —and many versions of those packages—could all be affected: which is exactly what many of this year’s incidents proved. All of this creates havoc in a security organization, and costs precious time when response speed is essential to mitigating an attack’s effects.
From Reactive to Responsive
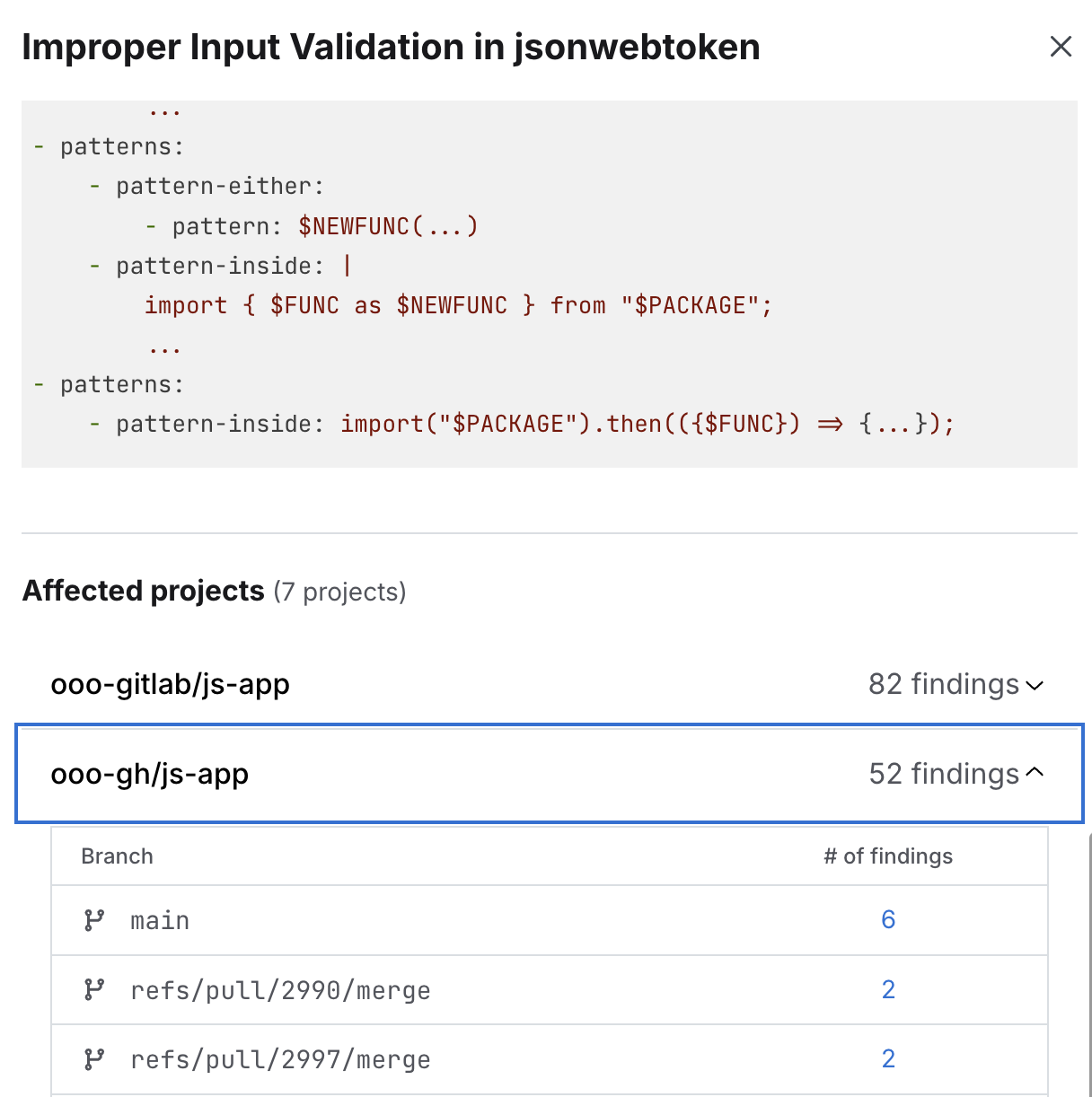
Semgrep Supply Chain’s advisory impact analysis helps AppSec quickly know if, and how, they’re affected by the latest supply chain attack. When Semgrep issues an advisory in response to a new CVE, e.g. during the latest malware incident, advisory impact analysis organizes scan results in a way that allows you to quickly search your environment for relevant findings. Using Semgrep Pro engine, it also pinpoints where exactly in your environment those findings lie. Whether you have a single, or multiple versions of an affected package, you can easily see down to the branch level any project where the new CVE may be exploited.