At its core, the Payment Card Industry Data Security Standard (PCI DSS) is about trust. Every time a customer swipes a card or taps to purchase with a phone, they trust that the elaborate web of payment infrastructure behind the transaction is secure. For fintechs and merchants alike, PCI DSS is the framework that validates that trust; it is a license to operate in the digital economy.
For years, maintaining that license has meant rigid checklists, "Code Freezes," and frantic paperwork. But the standard has evolved with the arrival of PCI DSS v4.0 (and the addendum v4.0.1), introducing the "Customized Approach," and acknowledging that modern AppSec teams might know how to secure their stacks in a better fashion than just a boilerplate checklist.
The "Screenshot Era" is over
In early 2025, practically yesterday in the compliance world, PCI DSS v4.0.1’s mandatory deadline came and went. With the panic of the initial migration gone, a new problem emerged: Operational Drag.
To pass the initial March audit, many teams leveraged the improved flexibility of the Customized Approach. They created manual "Targeted Risk Analysis" (TRA) documents to justify their controls and relied on one-off waivers to bridge gaps. While this satisfied the Qualified Security Assessor (QSA) at the time, maintaining those manual artifacts will become (or has already become) a time intensive job each audit. What was supposed to be a flexible framework has turned into technical debt.
Sustainable compliance requires treating the QSA like a software integration. You must stop writing policy documents and start shipping Policy-as-Code.
The automation scope: what can you actually code? While you can't automate everything, the "Software Security" domain is ripe for Policy-as-Code. Here is the engineering hit-list for v4.0.1:
Req 6.2.4 (Injection Flaws): Automate via SAST. Instead of manual code review, block SQLi/XSS in the PR.
Req 6.3.1 (Vulnerabilities): Automate via SCA. Shift from quarterly scans to continuous detection of CVEs and malicious packages.
Req 8.6.2 (Hardcoded Secrets): Automate via Secret Detection. Prevent keys from entering the repo entirely.
Req 6.3.2 (Inventory): Automate via SBOM generation.
Note: Other requirements, like 10.2 (Logging), can be automated via infrastructure-as-code (cron jobs, Terraform), but for this post, we are focusing on the source code itself.
The Shift: From "Gatekeepers" to "Guardrails"
Traditional compliance tends to act as a "Gate" at the very end of the SDLC. In this model, auditors or security engineers manually review changes before deployment. This creates a bottleneck and encourages developers to batch changes, making risk harder to manage.
PCI DSS v4.0.1 validates a different workflow: Guardrails.
Under the Customized Approach, you can demonstrate that an automated control in the CI/CD pipeline provides equivalent or superior security to a manual review. When you block a vulnerability at the Pull Request (PR) stage, you generate immediate, immutable evidence.
A "Gate" requires a human to write a report every time they check it. A "Guardrail" generates its own log evidence every time it runs.
Guardrails scale. Gates do not.
Automating the "Targeted Risk Analysis" (TRA)
One of the most significant changes in v4.0 was the introduction of the Targeted Risk Analysis (TRA). This allows organizations to define their own frequency (how often) and methods (how it's done) for specific controls, provided they document the rationale.
However, proving you followed your own customized rule is difficult with manual checks. If your TRA states that "Payment logic acts as a firewall for data types," an auditor will ask: "How often do you check this?"
The solution: Codify the TRA
Instead of relying on manual code review to enforce your TRA (which is slow and infrequent), use Semgrep to codify the requirement. This solves both variables:
The method: The code rule enforces your specific logic.
The frequency: The rule runs on every PR, proving the control is "continuous."
For example, consider PCI DSS Requirement 3.4, which mandates that PAN (Primary Account Number) is rendered unreadable anywhere it is stored. A common violation occurs when developers accidentally log payment objects for debugging purposes.
You can write a Semgrep rule to enforce this explicitly:
rules:
- id: no-payment-object-logging
patterns:
- pattern: logger.info($PAYMENT)
- pattern-inside: |
class PaymentController { ... }
message: "PCI DSS Req 3.4 Violation: Do not log payment objects!!! This may expose PAN data."
languages: [java, go, python]
severity: CRITICALNote: This rule logic is simplified for readability. In production, you would use more advanced syntax to specifically target objects of type com.stripe.model.Charge or similar, rather than blocking all logging within a controller.
When this rule runs in CI, it prevents the violation from merging. The evidence you provide to the auditor is no longer a policy document promising that developers are trained on secure logging. The evidence is the rule file itself and the CI logs and Semgrep Dashboard showing it is active.
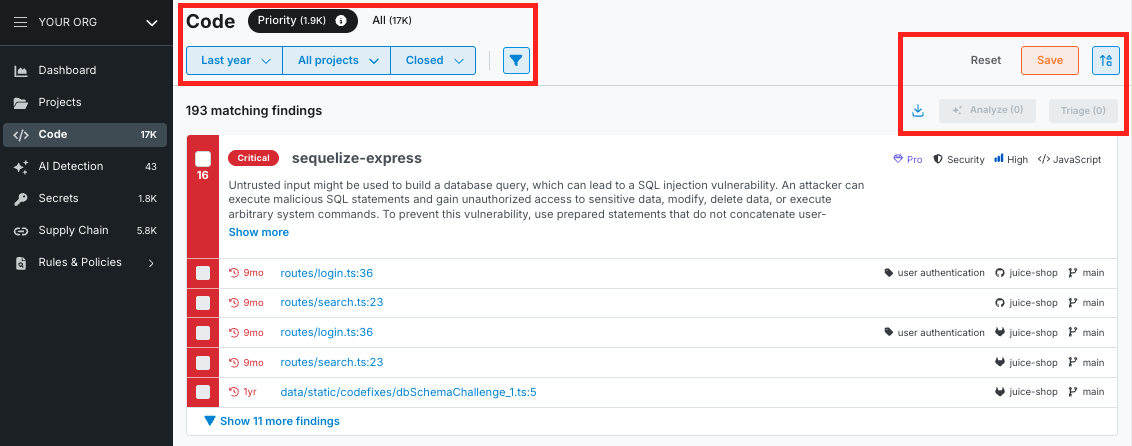 While no static rule catches 100% of complex operational logic, a targeted rule establishes a baseline 'Guardrail' that covers the majority of standard patterns. This allows manual reviewers to focus on the edge cases rather than the obvious violations.
While no static rule catches 100% of complex operational logic, a targeted rule establishes a baseline 'Guardrail' that covers the majority of standard patterns. This allows manual reviewers to focus on the edge cases rather than the obvious violations.
For complex apps, simple code scanning isn't enough. Use Semgrep's Interfile Taint Analysis to track 'untrusted data' (like a request body) as it flows between files through your app. If that data hits a 'sink' (like a raw SQL query or a log file) without being sanitized, Semgrep blocks it. This helps satisfy PCI Req 6.2.4 (Injection Flaws).
"Reachability" helps support your new waiver
Requirement 6.3.3 in PCI DSS v4.0.1 mandates that patches for Critical vulnerabilities be installed within one month of release.
Note the emphasis on Critical. The v4.0.1 update clarified that this 30-day SLA applies strictly to critical-severity issues, correcting earlier confusion that "High" severity issues might also be included.
Despite this clarification, modern applications still often pull in thousands of third-party dependencies. A standard SCA scan might report 100 "Critical" vulnerabilities in a large enterprise monorepo. Patching all 100 within 30 days is a challenge for most engineering teams without disrupting or halting feature work entirely.
The Old Way: You spend weeks arguing with the auditor, manually reviewing each vulnerability to prove it is not exploitable, and writing hundreds of "False Positive" waivers.
The Semgrep Way: Use Dataflow Reachability Analysis to bulk-downgrade the critical risk. Since PCI Req 6.3.3 strictly mandates a 30-day patch cycle for Critical vulnerabilities, proving a vulnerability is Unreachable effectively removes it from that 30-day clock.
Semgrep Supply Chain analyzes how your code uses open-source libraries. It builds a call graph to ensure the vulnerable function is executed, and it performs a data check (dataflow analysis) to verify that untrusted data actually reaches that function. It only alerts you if the path connects a specific known vulnerability to an unsafe data source.
If a library has a critical vulnerability but your code never calls the vulnerable function, the risk is significantly lower. Reachability Analysis provides the technical evidence to help justify not patching immediately.
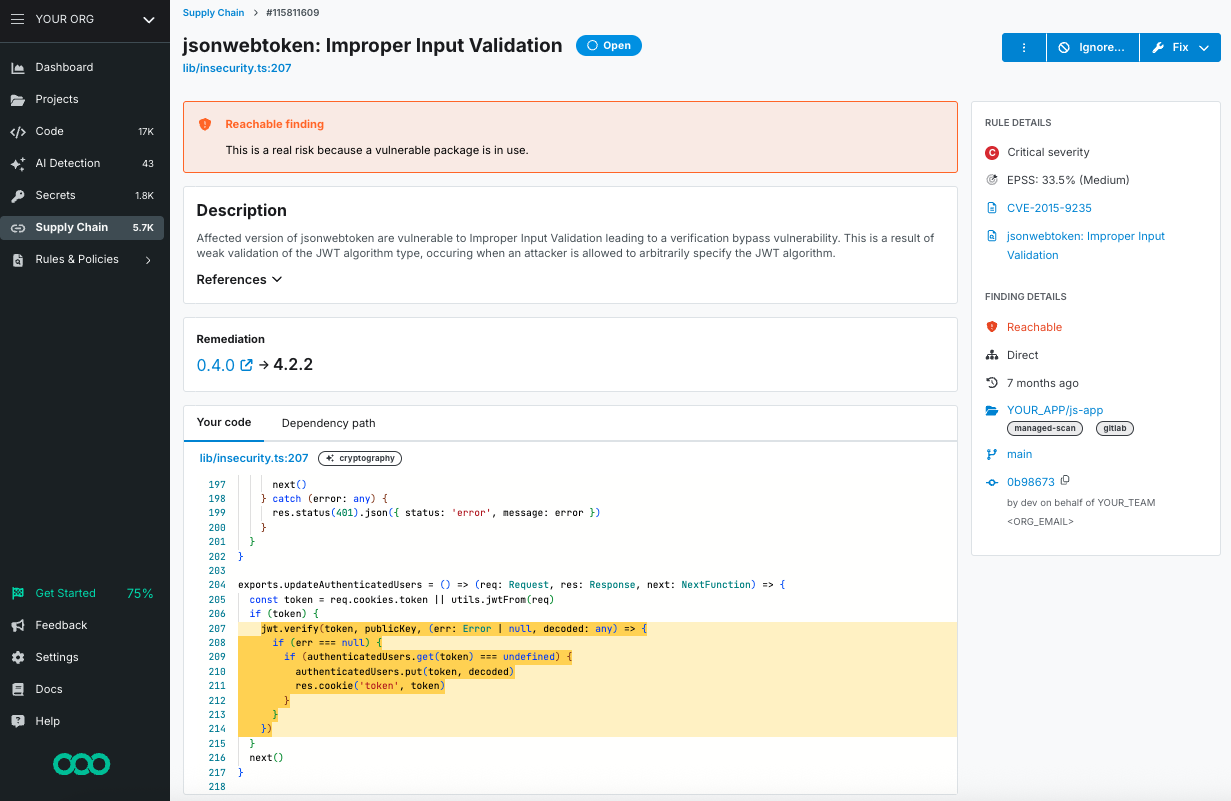 This helps the conversation with the auditor shift from "We didn't have time to patch" to "We have automated evidence that this vulnerability is unreachable in our Cardholder Data Environment (CDE)." This turns a compliance failure into a documented, risk-based decision.
This helps the conversation with the auditor shift from "We didn't have time to patch" to "We have automated evidence that this vulnerability is unreachable in our Cardholder Data Environment (CDE)." This turns a compliance failure into a documented, risk-based decision.
CVEs are only half the battle. Use Semgrep Supply Chain to catch "intentional" attacks (like typosquatting or malware) that standard SCA tools miss. Semgrep’s research team monitors the open-source ecosystem and community for alerts and updates our blocklist. This allows you to block malicious packages (like obfuscated code in post-install scripts) before they ever run, applying a 'Defense in Depth' strategy to help satisfy PCI Req 6.3 without slowing down your builds.
Secrets hygiene as a "DORA Metric"
Requirements 3.2 through 3.4 focus heavily on protecting Sensitive Authentication Data (SAD) and PAN. A frequent failure point in modern audits is the discovery of hardcoded secrets, API keys, test PANs, or Stripe tokens, in the git history.
Auditors in late 2025 are technically savvy. They understand that "code is storage." If a secret is committed to the repository, it is considered a violation, even if it was never deployed to production. Retroactively scrubbing git history is painful, disruptive, and often requires a difficult conversation with your QSA about why the secret was there in the first place.
The fix: pre-commit for speed, CI for audit
To satisfy the auditor while maintaining developer velocity, you need a dual-layer approach.
Local hygiene: Implement Semgrep Secrets as a pre-commit hook. This is a developer experience tool that prevents data from leaving the local machine.
Server-side enforcement (the control): Pre-commit hooks can be bypassed, so they are not a sufficient audit control on their own. You must enforce the block in your CI/CD pipeline. The auditor cares about the server-side CI log, which proves that no code, regardless of how it was committed, can merge with a live secret.
Reducing the noise Blocking builds is high-stakes, so you must distinguish between "noise" and "risk."
Generic secrets & AI filtering: For internal credentials that lack clear prefixes (like custom internal API tokens), simple entropy checks flag too much noise. Semgrep solves this by first detecting high-entropy strings, then applying AI classifiers to filter out false positives. This allows you to catch genuine custom secrets without blocking the build on every random Git hash or other random string.
Secret validation: Don't just detect; validate. Semgrep can automatically check if a detected credential is active by testing the credential with the provider (e.g., checking if that Stripe key actually works).
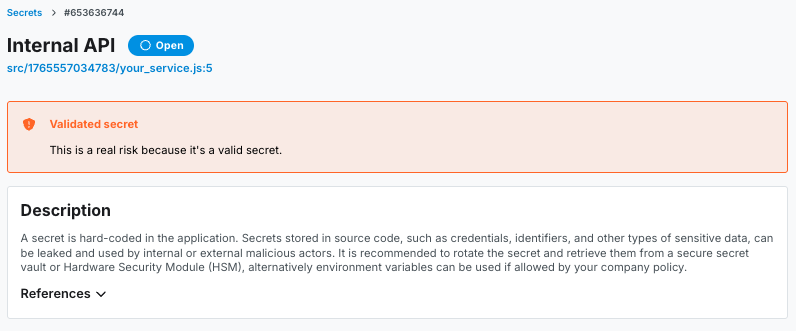 When you block valid secrets at the CI level, you ensure compliance. When you catch them at the pre-commit level, you ensure security without sacrificing speed. Doing both keeps your git history clean and avoids the "finding backlog" that plagues teams during the pre-audit scramble.
When you block valid secrets at the CI level, you ensure compliance. When you catch them at the pre-commit level, you ensure security without sacrificing speed. Doing both keeps your git history clean and avoids the "finding backlog" that plagues teams during the pre-audit scramble.
The "set it and forget it" evidence
The goal of operationalizing PCI DSS v4.0.1 is to reach a state where the audit requires low-to-no interruption to the engineering team. When the QSA asks for evidence, you should not need to search through Jira tickets or email developers.
Instead, you can quickly assemble your audit artifacts using Semgrep’s standard exports:
Policy configuration: Export your active Ruleset (or share your .semgrep.yml). This serves as your codified policy, proving exactly what you are checking for (e.g., "Block all unmasked PAN logging").
CI/CD block logs: These are your proof of enforcement. By showing a history of failed pipelines where Semgrep blocked non-compliant code, you demonstrate that your "Guardrails" are active, satisfying the requirement for continuous monitoring.
Reachability exports: Download your findings report (JSON/CSV) filtered by "Unreachable." This provides the data-backed justification for any Critical vulnerabilities that were not patched within the 30-day window, satisfying the Targeted Risk Analysis requirement for dependency management.
SBOM: Generate an automated, machine-readable inventory of all third-party software using the Semgrep CLI (semgrep ci --supply-chain --sbom) or via the dashboard. This satisfies Requirement 6.3.2 without manual spreadsheets.
Conclusion
You may never kill the spreadsheet entirely, but you can automate the data entry that fills them. By operationalizing PCI DSS v4.0.1, you turn compliance from a bottleneck into a background process:
Codify your TRA: Replace manual code reviews with custom rules that enforce logic like Requirement 3.4 automatically.
Leverage Reachability: Use data-flow analysis to prove to your auditor that hundreds of "Critical" vulnerabilities are unreachable, saving weeks of patching time.
Treat secrets as quality: Enforce pre-commit hygiene and server-side blocking to keep your git history clean and your audit findings empty.
Don't just survive the audit, engineer it away.
Leading fintechs like Airwallex didn't just "pass" their 4.0.1 audit; they used Semgrep to scale security across hundreds of developers without slowing down velocity. Read the Airwallex Case Study to see their blueprint for automated compliance.
Ready to build your own evidence pack? Visit our Compliance Documentation for a technical breakdown of how to map Semgrep features to PCI DSS, SOC 2, and ISO 27001 controls.




