Breadth and depth of Semgrep Supply Chain
We are excited to announce that Semgrep Supply Chain now has dataflow reachability coverage for Scala and Swift – users will now be able to see complete reachable and unreachable results in their Supply Chain findings.
With these two languages, and last month’s addition of Kotlin reachability, we now officially support full dataflow reachability for 10 languages, which reduces noise attributed to false positives by as much as 98%, saving hours of developer time so they can focus on the most impactful security risks.
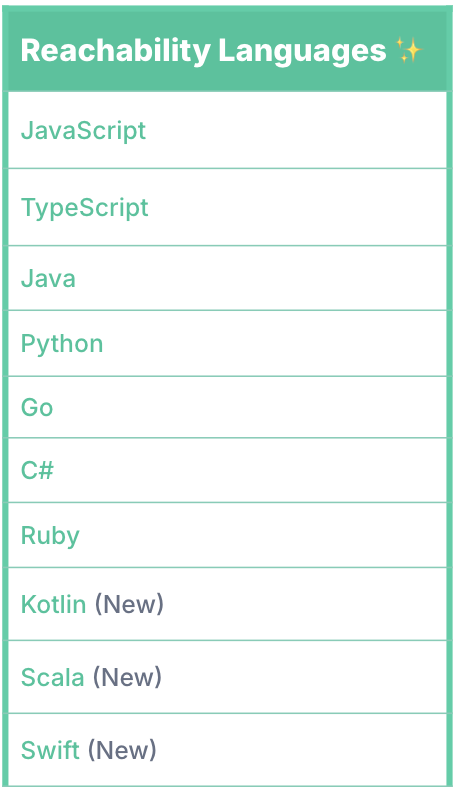 This makes Semgrep Supply Chain the market leader when it comes to reachability coverage in terms of breadth of coverage.
This makes Semgrep Supply Chain the market leader when it comes to reachability coverage in terms of breadth of coverage.
The next important feature to highlight relates to how we define dataflow reachability analysis and our depth of coverage. Our unique approach to reachability allows Semgrep to identify how you’re using a library and assess whether it is being used in a vulnerable way.
When a finding is reachable, it means that a team of Semgrep Security Researchers reviewed the security advisory, identified the affected functions, determined how they're vulnerable, and created Semgrep rules to detect if and how those functions are called in your code. We have written about reachability in the past, if you are looking for a refresher, and this post about how our Security Researchers write a Semgrep rule illustrate the advantages of dataflow reachability that help to reduce false positives.
By using an approach that prioritizes both breadth and depth, Semgrep reduces noise generated by false positives and scales to cover your entire code base.
10 reachability languages!
Getting to 10 languages has invited questions about why we prioritized these specific languages, and how we think about our approach to coverage. While a language's inclusion in the Semgrep engine and expanding our language coverage is one driver, we also have close partnerships with our customers and listen to the use cases they need addressed.
Another factor includes research into global adoption and popularity of a language; whether it be StackOverflow’s Global Developer Survey or DevJobScanner looking at how languages are listed in JDs. By no means do these measurements indicate the vulnerability risk of a language, but they do provide trend datapoints and patterns for us to evaluate. The long and short of it is that as languages grow, evolve, and become engrained amongst codebases, the need for robust SCA to identify vulnerabilities in third-party dependencies grows as well. For our 10 languages, we cover all new CVEs, with on-going work to extend our historical coverage.
Scala and Swift reachability
And now, for Scala and Swift.
Scala is one of the most popular functional programming (FP) languages and a common choice among developers who want an FP language that is very Python-like. Scala also has a supportive ecosystem of tooling, such as Scala CLI, IntelliJ IDEA, etc. Scala has a small but mighty community. Part of how this community developed is because Scala runs on the Java Virtual Machine (JVM) which has helped its adoption. Running on the JVM cuts both ways though: it also means Scala has inherited JVM vulnerabilities while there are fewer dedicated Scala SCA solutions than in the Java community.
Swift, originally created by Apple as an open source programming language alternative to Objective-C, C++, and C, is a highly popular statically typed language for developing mobile applications. While it incorporates a few security forward practices, with accommodations made for memory management (like buffer overflows), as well as a strong static typing system that can catch many errors at compile time, there have also been some critical vulnerabilities introduced via package managers like CocoaPods that are entirely due to open source dependencies.
Semgrep comes to market with 100% rule coverage for critical and high CVEs for Swift. We also have 100% coverage for 2024 and 2023 for Scala. Prior years for Scala have varying percentages for coverage and we are actively backfilling coverage back to 2017.
Community feedback
We’ve heard feedback from the Semgrep Slack community on bringing Swift and Scala to market.
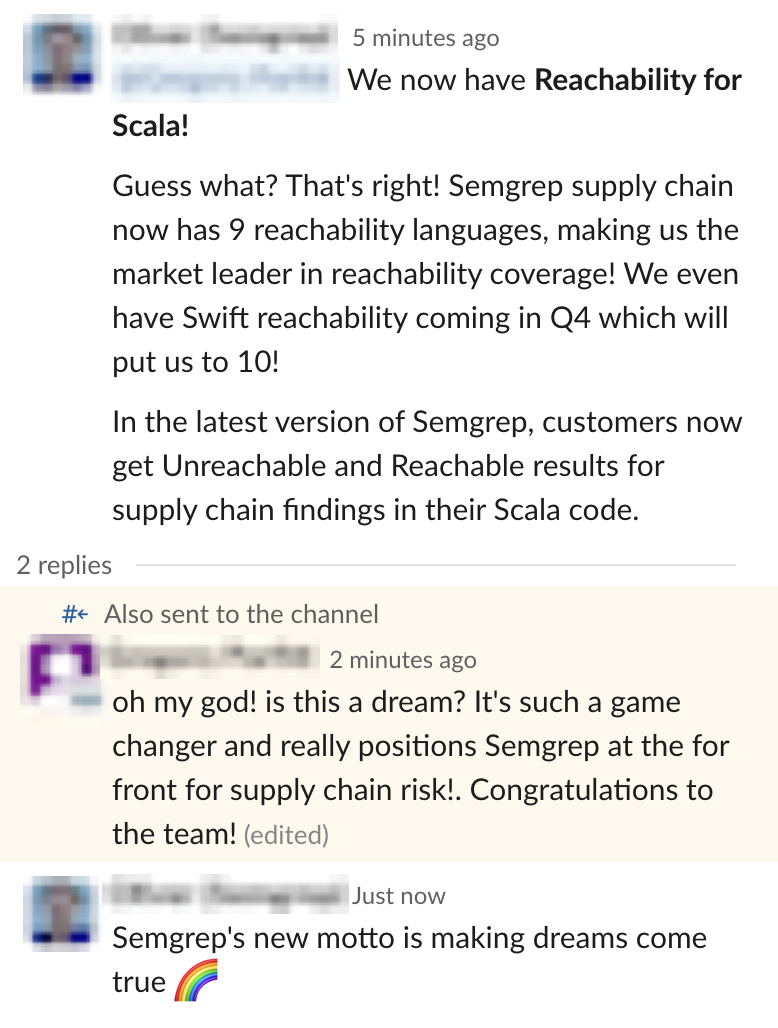 We won’t name names, but we did have a senior leader question if our members should dream bigger. (The Supply Chain team does disagree and endorses these dreams as exactly the right dreams)
We won’t name names, but we did have a senior leader question if our members should dream bigger. (The Supply Chain team does disagree and endorses these dreams as exactly the right dreams)
What’s next?
In addition to the broad coverage across languages and ecosystems, we cover historical vulnerabilities across these ecosystems. Check out our page for Supported Languages to keep up to date with our latest releases and learn more about our coverage!
We remain focused on breadth and depth: expansion of reachability coverage and expansion of historical coverage per language. While we are currently at 10, we are committed to a continued partnership with our customers to bring more languages to market. Whether you’re a large corporation with a code base of many languages or you only have a few, all parties can be assured that Semgrep meets their needs.
We are really excited about bringing this coverage to market. Internally, we have added a Taylor Swift emoji to our Slack instance, but we can only speculate as to her endorsement of Swift on Semgrep Supply Chain. Try out dataflow reachability on any, or all, of our 10 languages today; and as always, please let us know what you think!





