We are excited to introduce the integration of FIRST's Exploit Prediction Scoring System (EPSS) into Semgrep Supply Chain. All findings now include the advisory’s associated EPSS score, updated daily to reflect the latest predictive insights from the EPSS model.
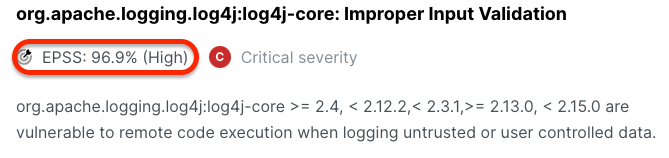 EPSS is a powerful prioritization mechanism: when combined with Semgrep’s dataflow reachability analysis, EPSS enables you to deprioritize 99% of findings and focus on the 1% that matter most.
EPSS is a powerful prioritization mechanism: when combined with Semgrep’s dataflow reachability analysis, EPSS enables you to deprioritize 99% of findings and focus on the 1% that matter most.
The Exploit Prediction Scoring System (EPSS)
EPSS, developed by FIRST, assesses the likelihood that a vulnerability will be exploited within the next 30 days. This tool uses a machine learning model that draws from a wide array of real-world data, such as CISA’s Known Exploitable Vulnerability (KEV) database and publicly available exploit code, providing dynamic scores that adapt to the evolving threat landscape. It serves as a critical prioritization tool, enabling security teams to focus on vulnerabilities that pose the most immediate risk of exploitation.
And who is FIRST? The Forum of Incident Response and Security Teams (FIRST) is a global group of security and incident response teams dedicated to improving cybersecurity worldwide. FIRST plays a crucial role by providing a platform for experts to discuss and address emerging threats, vulnerabilities, and incident response strategies.
What EPSS is not
While EPSS is a valuable tool for predicting the exploitability of vulnerabilities, it is important to understand its limitations. This understanding helps to ensure that it is used effectively within the broader context of an organization’s security strategy:
Not customized for individual codebases: EPSS does not evaluate the exploitability of vulnerabilities based on the unique characteristics of your specific project. It provides a generalized forecast of the probability of exploitation for vulnerabilities that are already known to be exploitable.
Not a guarantee of future exploits: While EPSS predicts the likelihood that certain vulnerabilities might be exploited, it does not confirm that any particular vulnerability will definitely be exploited or not.
Not an indicator of severity: EPSS focuses on the likelihood of exploitation, not the vulnerabilities' severity or class (e.g., Denial of Service vs. Remote Code Execution). It should not be used as the sole criterion for assessing a vulnerability's impact. Other tools and frameworks, such as CVSS, are better suited for understanding a vulnerability's potential damage or impact. Semgrep findings include a measure of severity based on the GitHub Advisory Database.
How to use EPSS to prioritize?
Open source vulnerability scanners are crucial for maintaining robust application security. Yet, they often inundate security teams with alerts, exaggerating the risk level of known vulnerabilities. Semgrep Supply Chain addresses the challenge of too much noise with our reachability analysis feature, which reduces false positives by over 90% compared to traditional scanners, leaving a manageable number of actionable findings.
Despite this significant reduction, the question remains: among the reachable vulnerabilities, which should be addressed first? Triaging this list is where the value of EPSS comes into play. By predicting which vulnerabilities are most likely to be exploited, EPSS enables teams to focus on the most important issues first, and ensure that resources are allocated where they are needed most. Especially when you consider only ~6% of known CVEs end up being exploited.
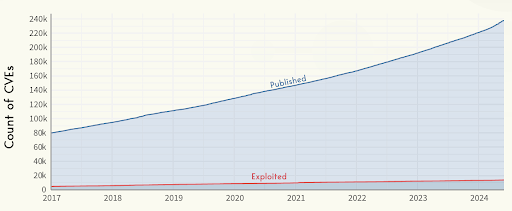 Cyentia Institute: The Inaugural study of EPSS Data and Performance
Cyentia Institute: The Inaugural study of EPSS Data and Performance
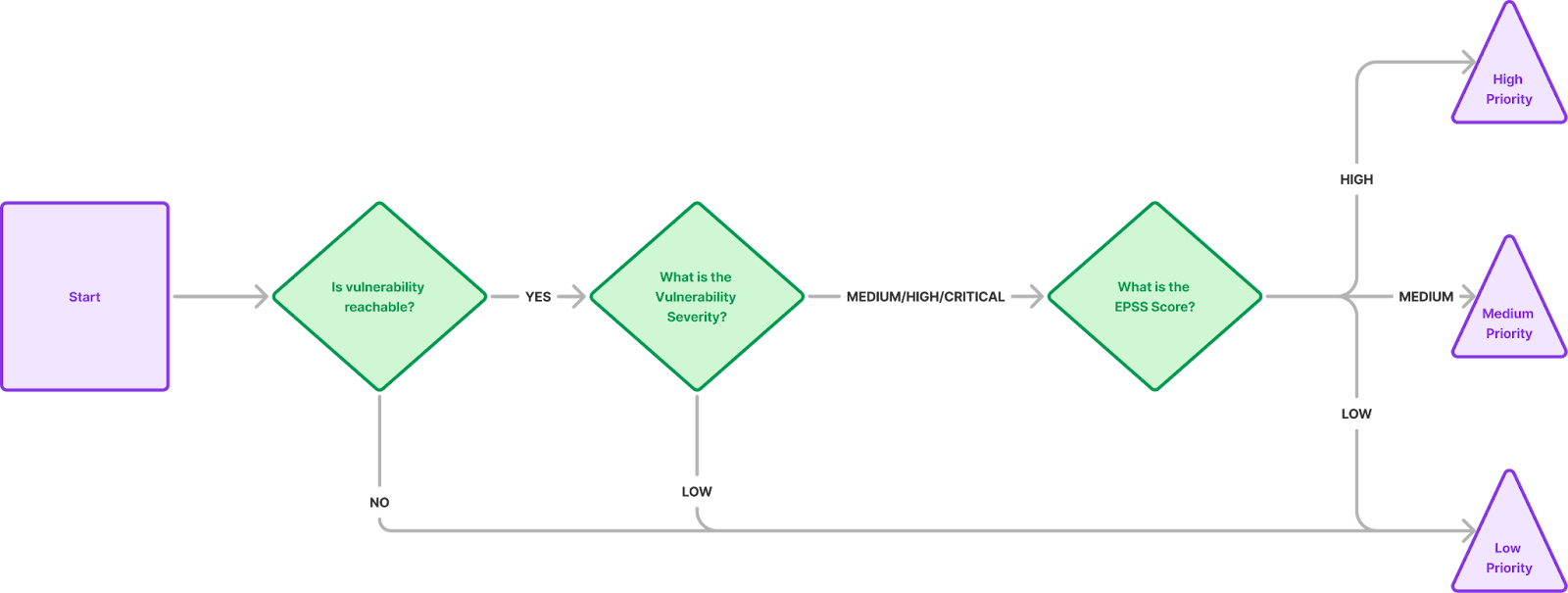
An example of using EPSS for prioritization is through a decision tree approach. First, leverage Semgrep’s reachability analysis to determine if a vulnerability is used within your environment in a vulnerable way. For all medium to critical findings based on CVSS or the GitHub Advisory Database, apply the EPSS score to evaluate the likelihood of exploitation in the near term. This structured process helps security teams focus on the most pressing vulnerabilities, ensuring that remediation efforts are both strategic and impactful.
Conclusion
EPSS has proven its effectiveness in predicting exploit likelihood, making it an invaluable tool for prioritizing the remediation of security vulnerabilities. For more insights into how EPSS can transform your vulnerability management strategy, check out FIRST’s user guide.
And for more insight into how Semgrep’s application of EPSS can actively impact your own team, try it out. Get prioritizing. Or get a hold of us for a demo.




