Create a Semgrep account and set up organizations
- You have gained the necessary resource access and permissions required for deployment.
Create a Semgrep account by signing in to Semgrep AppSec Platform with your GitHub or GitLab account. This enables you to:
- Add the rest of your GitHub or GitLab organization (org) members to Semgrep.
- Configure Semgrep to scan repositories in other source code managers, such as Bitbucket.
Alternatively, reach out to sales@semgrep.com to set up SSO. This removes the need to sign in through a GitHub or GitLab account if you don't have one.
Semgrep AppSec Platform
Semgrep AppSec Platform is used to manage all Semgrep products, and it is where you can:
- View and manage your Semgrep findings.
- Customize how Semgrep scans your code.
- Manage the users associated with your Semgrep organization.
- Set up alerts and notifications, including Slack alerts, emails, and pull request or merge request comments pushed to your source code manager
Initial sign in to Semgrep AppSec Platform
The following steps walk you through creating a user account and your first organization:
- Sign in with GitHub
- Sign in with GitLab
To sign in using your GitHub account:
- Navigate to the Semgrep AppSec Platform login page and click Sign in with GitHub.
- Click Authorize semgrep-app to grant Semgrep the needed permissions and proceed.
- Enter an organization name when prompted then click Create new organization. This organization name is typically the name of the org in GitHub that you want to connect Semgrep to. For individual users, this can also be a personal account.
- Either select a scan environment or click Don't want to connect to anything yet?

- If you selected a scan environment:
- Follow the prompts to set up the scan.
- If you clicked Don't want to connect to anything yet:
- Choose either Skip setup if you prefer not to scan anything yet or See demo project to view how Semgrep scans and presents findings from a demo
juice-shopproject.
- Choose either Skip setup if you prefer not to scan anything yet or See demo project to view how Semgrep scans and presents findings from a demo
To sign in using your GitLab account:
- Navigate to the Semgrep AppSec Platform login page and click Sign in with GitLab.
- Click Authorize to grant Semgrep the needed permissions and proceed.
- Enter an organization name when prompted then click Create new organization. This organization name is typically the name of the org in GitLab that you want to connect Semgrep to. For individual users, this can also be a personal account.
- Either select a scan environment or click Don't want to connect to anything yet?

- If you selected a scan environment:
- Follow the prompts to set up the scan.
- If you clicked Don't want to connect to anything yet:
- Choose either Skip setup if you prefer not to scan anything yet or See demo project to view how Semgrep scans and presents findings from a demo
juice-shopproject.
- Choose either Skip setup if you prefer not to scan anything yet or See demo project to view how Semgrep scans and presents findings from a demo
You have successfully created an account, your first organization, and have optionally run your first scan.
Set up organizations
Organizations (orgs) in Semgrep enable users to share access to, and management of, Semgrep resources such as findings and reports.
Semgrep organizations can be connected to equivalent GitHub, GitLab, and SSO organizations, which enables users from those organizations to easily join your Semgrep deployment through their existing credentials.
Next steps for GitHub and GitLab users
- Connect your Semgrep org to your GitHub or GitLab SCM. Refer to Connect a source code manager for steps.
Next steps for Bitbucket and Azure Repos users
- Connect your Semgrep org to your Bitbucket Data Center project or your Azure DevOps project. Refer to Connect a source code manager for steps.
- To add members to your Semgrep organization, set up SSO authentication.
- You can also opt to scan a repository instead.
Appendices
These sections are helpful, but are not necessary to set up a deployment.
How Semgrep organizations work
Users can have more than one organization, and an organization can consist of one or many user accounts. Users must belong to at least one organization when they first sign in to Semgrep.
Organizations can be as small as a single user in a department, or encompass whole companies.
By default, orgs do not manage any authentication or repositories. You add resources and users to an org by connecting to an SCM or SSO, or setting up a Semgrep scan.
Once you have connected to your SSO or SCM, any team member from your GitHub, GitLab, or SSO organization can sign in to Semgrep. This includes developers not part of your security team. To control which resources they are able to see or what policies they can change, configure their role through user access control features.
Create additional orgs
After you create your first org, you can create multiple orgs to group related resources together:
- In Semgrep AppSec Platform, click the drop-down box with your organization name, located at the sidebar.
- Click Add org.
- Click Create an organization.
- In the popup, provide an Organization display name.
Organization setup examples
The following examples illustrate what a completed organizational set-up can look like.
Single-user organization in GitLab
- In this example, a single GitLab user,
john-doe, has a Semgrep org account with the same name. - He has set up his CI workflow to scan
repo-Aandrepo-Bin his GitLab account. The CI job sends scan results (findings) to Semgrep AppSec Platform. - This is similar to a personal account in GitHub or GitLab.
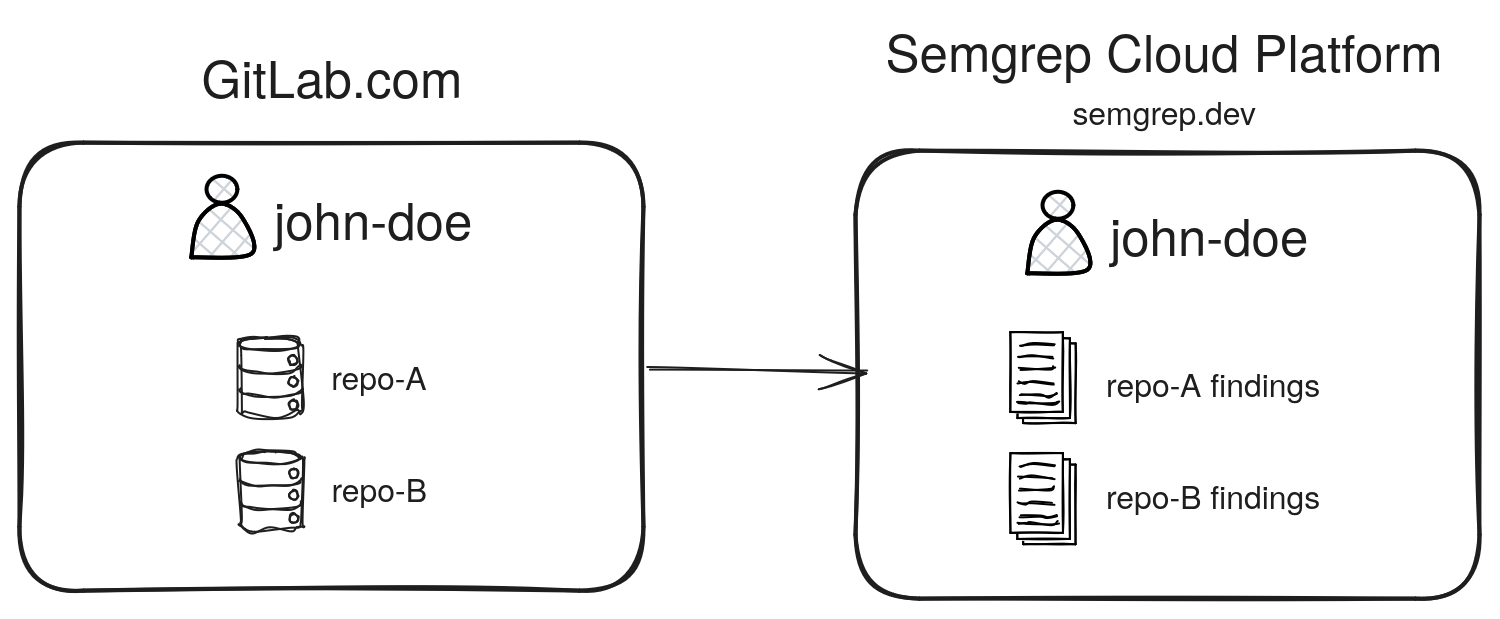 Figure. A simple example of a single-user, single-org setup (a personal account).
Figure. A simple example of a single-user, single-org setup (a personal account).
Enterprise org with SSO and multiple orgs in GitHub
In this example, a parent-company has multiple subsidiaries, and wants to use SSO for user authentication:
- Each
subsidiaryis its own GitHub organization. - The security team is responsible for all
subsidiariesinparent-company. Thus, the security team is a part of allsubsidiaries. - The
parent-companyenforces SSO for all of itssubsidiaries. - Here, membership and repository scanning are separately managed by two different services.
The Semgrep deployment could look like this:
- Each GitHub org has a corresponding Semgrep org.
- The security team has configured SSO for each Semgrep org.
- This means that
team-member-Rcan also accesssubsidiary-1-org. The resources they are able to view or change can be constrained through roles.
- This means that
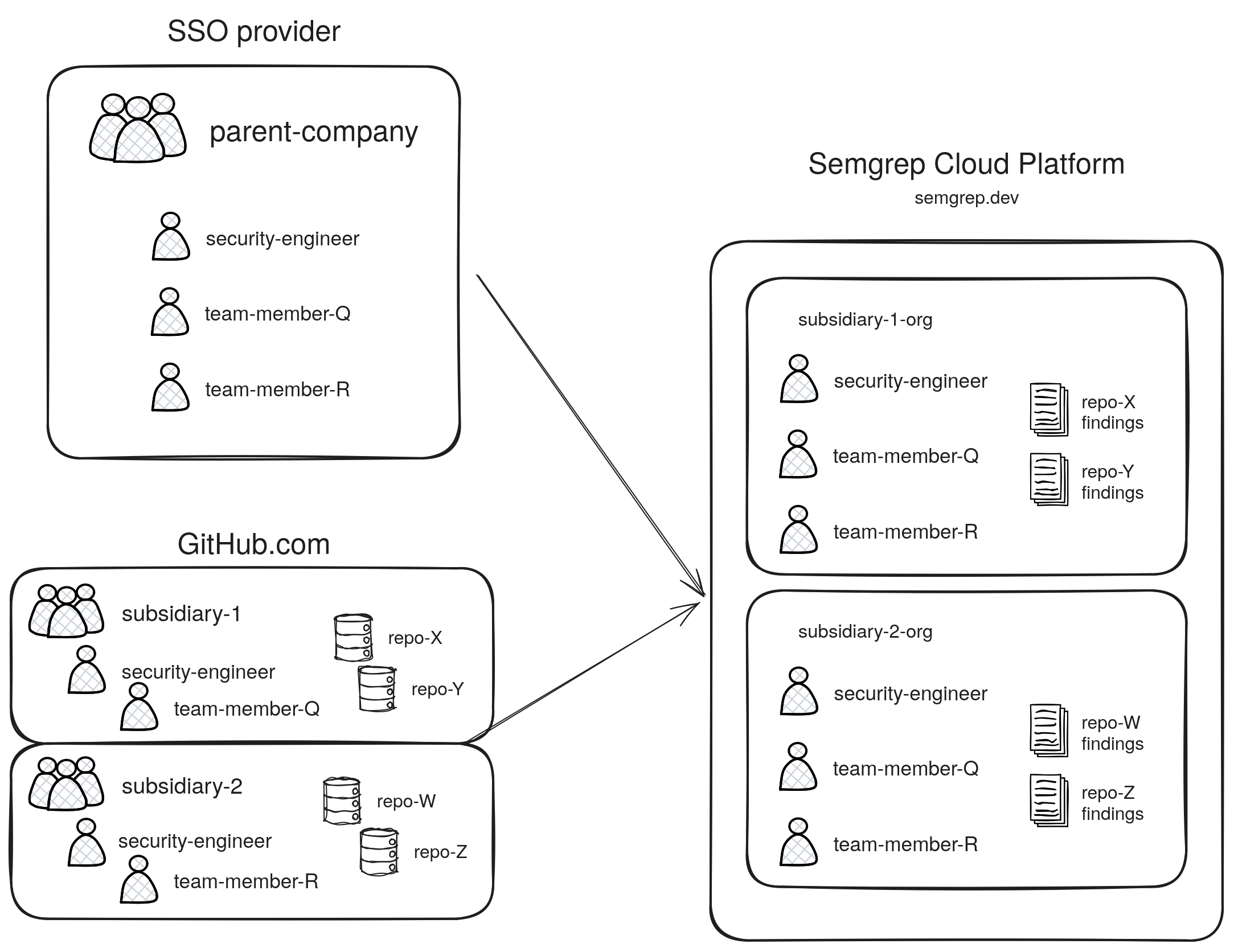 Figure. A complex organization setup using SSO and multiple GitHub orgs.
Figure. A complex organization setup using SSO and multiple GitHub orgs.
Join an existing org
Team members can join a Semgrep organization by logging in through the auth provider specified by their AppSec engineer:
- GitHub or GitLab
- SSO
To join an existing org in GitHub or GitLab:
- Sign in to Semgrep AppSec Platform with the account credentials specified by your admin.
- Follow the on-screen prompts to grant Semgrep the needed permissions and proceed. This creates your personal Semgrep account.
- Click Join an existing organization.
- Click your organization's name. The web app signs you in to your organization's Semgrep account. You can verify this by viewing the account name in the navigation menu.
To join an existing org through your SSO provider:
- Sign in to Semgrep AppSec Platform with the account credentials specified by your admin.
- You are automatically signed in to all organizations that your admin has set up for you.
AppSec engineers can also send developers invites to join their Semgrep org.
Delete an existing org
Reach out to support@semgrep.com to delete an organization.
Not finding what you need in this doc? Ask questions in our Community Slack group, or see Support for other ways to get help.