October 2023
· 4 min read
The following updates were made to Semgrep in October 2023.
🔧 Semgrep OSS Engine
- The following versions of Semgrep OSS Engine were released in October 2023:
🌐 Semgrep Cloud Platform
Added
- Added a button to Remove source code manager (SCM) apps. This is helpful when you have a misconfigured SCM app, such as GitHub's
semgrep-app, and want to reinstall it. To remove an SCM, click Settings > Source code managers.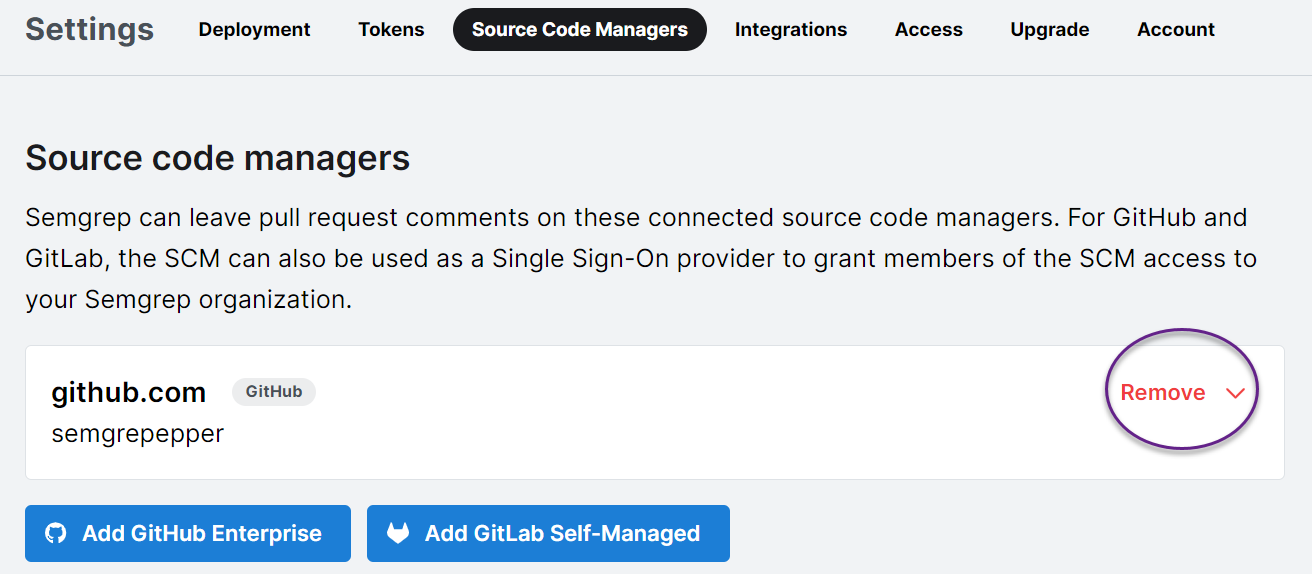
- Added Semgrep Assistant to the new Getting started guide in the onboarding flow.
- OpenAPI: Renamed instances of r2c to Semgrep.
- CLI login: New users are now directed to create a Semgrep org when they are logging in for the first time to Semgrep Cloud Platform from the CLI.
Changed
- Updated the default CircleCI YAML snippet to include full and diff scans.
Fixed
- Fixed UI issues in the new onboarding flow.
- Fixed an issue where Semgrep Cloud Platform could crash during the onboarding flow.
- Various frontend fixes and improvements to the following:
- Finding detail page
- Projects page
- Fixed an issue where the Delete user functionality did not work for some Semgrep orgs.
💻 Semgrep Code
Fixed
- Speed and stability improvements across the product. Semgrep Code pages, such as Findings and Policies, now load faster.
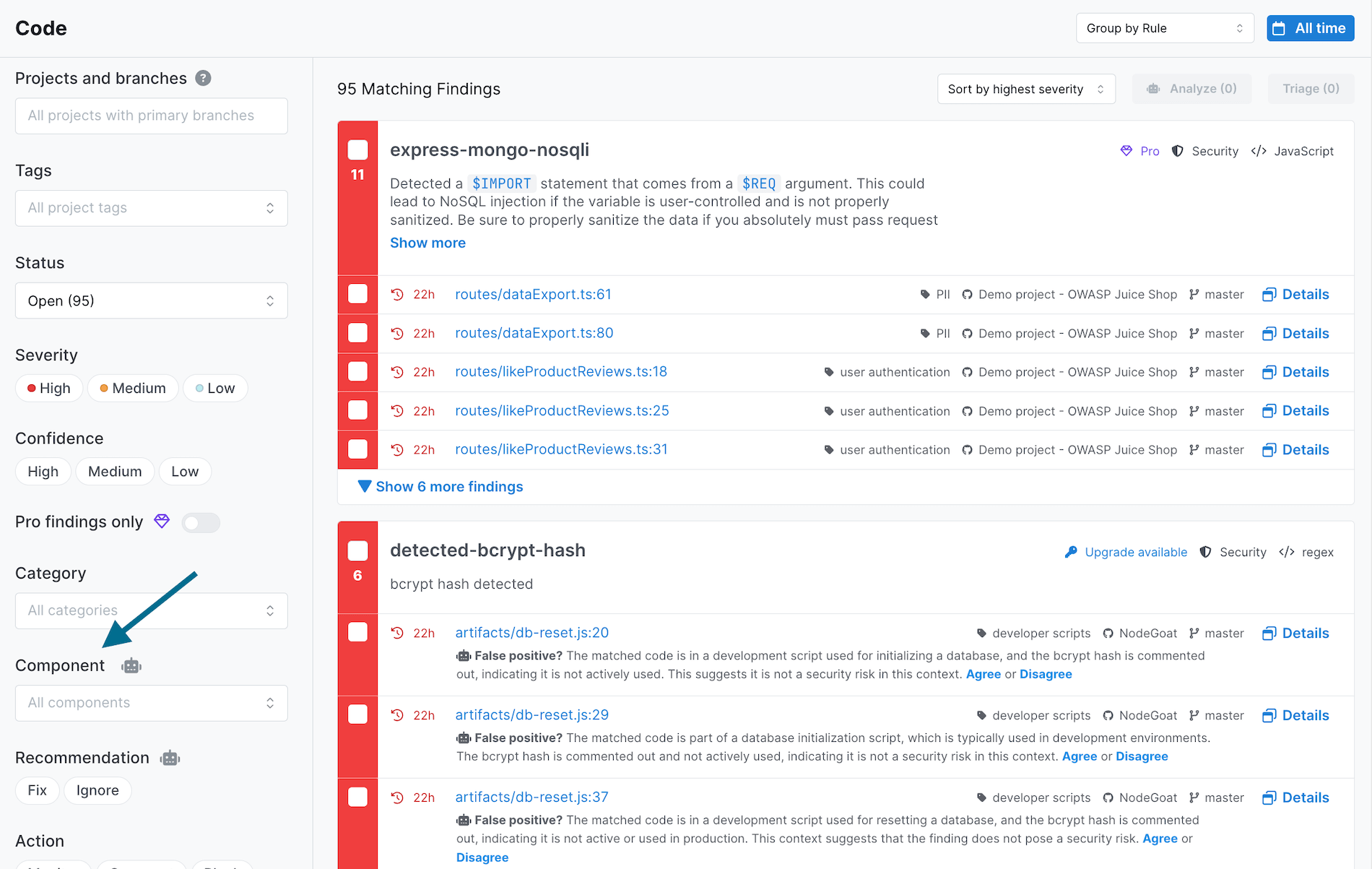
- Semgrep Assistant: Component tags are now visible for all Assistant users.
- Component tags use GPT-4 to categorize a finding based on its function, such as:
- Payments
- User authentication
- Infrastructure
- By categorizing your code through component tags, Semgrep Assistant is able to help you prioritize high-risk issues, for example if Semgrep has detected a code finding related to payments or user authentication.
- Component tags use GPT-4 to categorize a finding based on its function, such as:
⛓️ Semgrep Supply Chain
Added
- Added a new, public Semgrep Supply Chain API where you can filter and query third-party vulnerability findings by a variety of parameters, such as:
- Severity
- Repository
- Exposure
- C# reachability is now GA (generally available). Semgrep Supply Chain has added reachability rule support for all C# CVEs from May 2022 onward.
- SBOM export: Add vulnerabilities enriched with reachability analysis to export SBOMs.
- Dependency license scanning:
- Added support for NuGet (C#) license detection.
- Added support for RubyGems (Ruby) license detection.
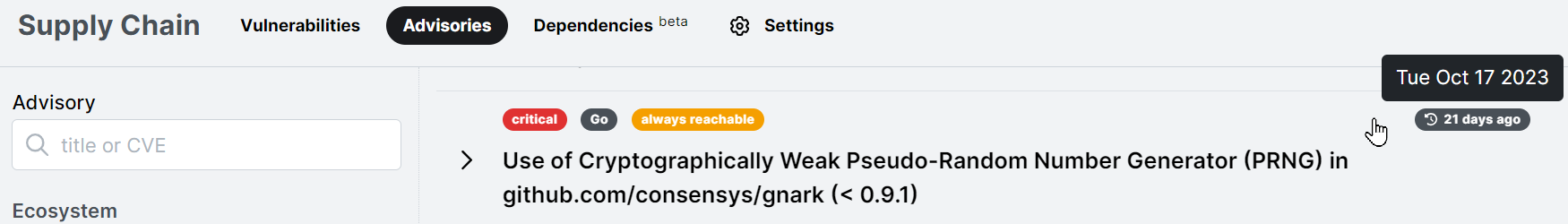
- Advisories: Added a tooltip displaying the date when a CVE Numbering Authority (CNA) created the security advisory. CVE Numbering Authorities include the MITRE Corporation. These dates are not assigned by Semgrep, Inc.
Changed
- SBOM (software bill of materials) export: The name of the exported SBOM file now follows the following format:
sbom-<org_name>-<repo_name>-<MM-DD-YY_H-m-s>--<serial_number>.<xml|json>
Fixed
- SBOM export: Fixed an issue where SBOM export failed when encountering dependencies with empty names.
- Vulnerabilities page: Fixed an issue where triage states did not update until a page refresh. Triage states now update as the user performs a triage action.
🔐 Semgrep Secrets (beta)
Added
- Semgrep Secrets is now in public beta.
- Projects page: Added a new column to display a Semgrep Secrets counter. This counter counts all secrets regardless of validation state.
Fixed
- Fixed links to branches in GitLab self-hosted repositories.
📝 Documentation and knowledge base
Added
- Added Semgrep Secrets documentation:
- Added Repository rulesets knowledge base article. This article explains how to scale Semgrep across many GitHub repositories.
- Created an automated job to sync the help output of the Semgrep CLI tool with CLI reference.
Changed
- The Policies documentation has been improved.
Fixed
- Various improvements to knowledge base articles.