Triage secrets findings in Semgrep AppSec Platform
After each scan, your findings are displayed in Semgrep AppSec Platform's Secrets page. The filters provided allow you to manage and triage your findings.
Findings from local scans are differentiated from their remote counterparts through their slugs. Remote repositories are identified as ACCOUNT_NAME/REPOSITORY_NAME, while local repositories are identified as local_scan/REPOSITORY_NAME.
Default Secrets page view and branch logic
In Semgrep, a single finding may appear in several branches. These appearances are called instances of a finding. In Semgrep Secrets, the latest instance, or the finding from the most recent branch scanned, is displayed by default. This is because, if a Secrets finding is present in any branch, even a non-primary (default) branch, it is considered valid.
Time period and triage
Quickly view all the findings your organization has fixed in a previous time period, such as a quarter or half-year, by using this filter.
The time period filter allows you to see which vulnerabilities were opened, fixed, or triaged during a certain period of time. The time period filter is not additive; it is a filter operation that precedes other filters on the page. For example, if you select Last triaged and select the status Status Open filter, no findings appear because, by definition, there are no triaged findings that are also open.
The following filters are available:
- Triage state:
- Last opened
- Last triaged
- Last fixed
- Time period:
- Last day
- Last 7 days
- Last 30 days
- Last 3 months
- Last 6 months
- Last year
- All time
 Figure. Time period and status filters.
Figure. Time period and status filters.
Export findings
You can export findings to a CSV file. Semgrep can export up to 10,000 most recent findings. To export more than 10,000 findings, you must use the API.
Semgrep exports all findings to the CSV file regardless of the filters you apply on the page.
Export findings by navigating to the product page and clicking the icon near the time filters.
 Figure. The download findings CSV button.
Figure. The download findings CSV button.
Click to view a description of fields included in the CSV.
| Field | Description |
|---|---|
| Id | The unique ID number of the finding. |
| Rule name | The name of the rule. |
| Product | The Semgrep product. Possible values are Code, Supply Chain, or Secrets. |
| Severity | The finding's severity. Possible values are Critical, High, Medium, or Low. |
| Status | The finding's triage status. |
| Assistant component | A descriptor, such as API, Payments processing, Infrastructure, that Assistant tags the finding with, based on the code's context. |
| Repository name | The name of the repository where Semgrep found the finding. |
| Repository URL | The repository URL. |
| Line of code URL | The URL to the specific line of code where the finding match began. A finding may be several lines long. |
| Semgrep platform link | A link to the finding's Details page in Semgrep AppSec Platform. |
| Created at | The time the finding was created in your timezone. |
| Last Opened at | The time the finding was last opened. |
| Branch | The name of the branch where the finding was detected. |
| Triaged at | The most recent time that the finding was triaged. |
| Triage comment | A triage comment created by the user. |
| Triage reason | The reason why the finding was triaged, created by the user. |
| Rule description | The description of the rule. This is the same as the rule's message key. |
The following fields are exclusive to Code scans:
| Field | Description |
|---|---|
| Confidence | The finding's confidence. Possible values are High, Medium, or Low. Only Semgrep Supply Chain and Code findings provide this field. |
| Category | The finding's category, such as best practices, security, or correctness. |
| Is pro rule | Boolean value that returns TRUE if the rule that generated the finding is a pro rule. |
| Assistant triage result | Provides Semgrep Assistant's assessment. Possible values are True positive or False positive. These values appear only if Assistant is enabled. |
| Assistant triage reason | A short AI-generated reason why Assistant thinks the finding is a true or false positive. These values appear only if Assistant is enabled. |
The following fields are exclusive to Supply Chain scans:
| Field | Description |
|---|---|
| Dependency | The name of the dependency where the findings was found. |
| Reachability | The reachability status of the finding, such as Reachable, No Reachability Analysis, or Unreachable. |
| Transitivity | States whether the finding originates from a direct or transitive dependency. |
| CVE | The CVE number that the finding is assigned to. |
| EPSS | The EPSS score, which estimates the likelihood that a software vulnerability can be exploited in the wild. |
The following fields are exclusive to Secrets scans:
| Field | Description |
|---|---|
| Secret type | Possible values include AI-detected, Generic secret, Connection URI, and so on. |
| Validation | States whether or not the secret was validated. |
| Project visibility | States whether the project (repository) is public or private. This feature supports GitHub-hosted repositories only. It returns an Unknown value for non-GitHub SCMs. |
Triage findings
You can triage secrets-related findings in Semgrep AppSec Platform on the Secrets page. By default, all findings are displayed. A common triage workflow includes the following tasks:
- Filtering for a particular characteristic of a finding, such as its Validation status, Repository or Branch, or Type.
- Analyzing if the findings are true or false positives.
- Applying a triage state to the filtered findings based on the analysis in step 2.
- Setting a finding as Ignored means that no action is undertaken and the finding is closed. Subsequent scans won't include this finding.
- Setting or retaining a finding as Open, Reviewing, or Fixing means that the finding is a true positive and needs to be fixed or resolved.
- Optional: You can create a ticket in Jira to assign a developer to fix findings.
When commits are added to the PR or MR, Semgrep re-scans the PR or MR and detects if a finding is fixed, or if the secret is no longer valid. The finding changes status automatically upon scanning. Users do not need to set a finding as Fixed manually.
Common filtering use cases
You can find and perform bulk operations through filtering; all filter operations are available to you on the Secrets page.
| Task | Steps |
|---|---|
| Viewing valid findings | Under Validation, click ⚠️Confirmed valid. |
| View findings in a specific project or branch | 1. Under Projects, select a repository from the drop-down menu. 2. Under Branches, select a branch from the drop-down menu. |
| View findings of a specific type of secret, such as personal token or password. | Under Type, select a type of secret. |
| View findings of a specific severity | Under Severity, select a value. |
 Figure. Secrets page and relevant triaging elements: (a) All available filters; (b) Bulk selection toggle; (c) Bulk triage button.
Figure. Secrets page and relevant triaging elements: (a) All available filters; (b) Bulk selection toggle; (c) Bulk triage button.
You can triage findings in bulk by performing the following steps:
- Begin by ensuring that you display all Open findings.
- Apply filters with as much specificity as possible. You may have to perform bulk triage several times. By starting with the most specific cases, and closing the findings from those specific cases, you are able to narrow down findings as you work from specific to broad filter criteria.
- Click the bulk select check box.
- Click Triage, then your selected triage state, such as Reviewing or Ignored.
- Optional: Repeat this procedure to triage all open findings.
Receive findings through PR and MR comments
In addition to viewing your results in Semgrep AppSec Platform, you can set up PR or MR comments from Semgrep, which allows you to view findings-related information directly in your pull requests and merge requests.
To receive PR or MR comments, ensure that:
- You have set up comments as part of your core deployment.
- You have defined which rules and validation states should be in Allow, Comment, or Block mode in the Policies page.
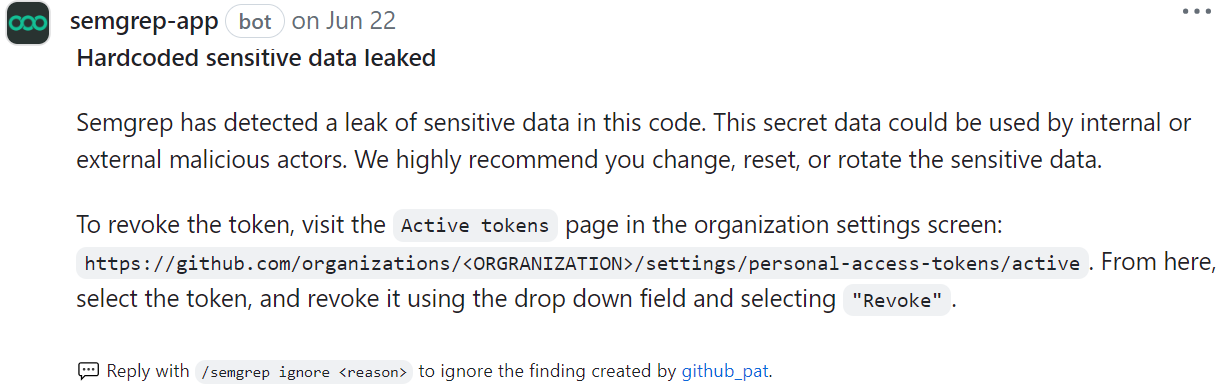 Figure. Semgrep Secrets finding in a PR comment.
Figure. Semgrep Secrets finding in a PR comment.
Define which rules and validation states should be in Allow, Comment, or Block mode in the Policies page.
Not finding what you need in this doc? Ask questions in our Community Slack group, or see Support for other ways to get help.